What’s Your Plan to Beat the Monsters of Cybersecurity?

Incident Response Planning is Critical for Incident Recovery
Cybercrime numbers are soaring, putting pressure on businesses and IT teams alike to stay a step ahead of the bad guys. An estimated 74% of organizations in the United States have fallen victim to a successful phishing attack that resulted in a data breach in the last 12 months and phishing is up by almost 300% over 2020’s record-breaking numbers. No business is too small to be a target, and no industry is safe from the laser eye of greedy cybercriminals. Plus, the specter of a devastating ransomware attack is at the top of every IT professional’s mind after high-profile events in the last two years have made it the cyberattack that everyone is talking about.
This post is excerpted in part from our scary good eBook Monsters of Cybersecurity. DOWNLOAD IT>>
Your Next Incident is a Click Away
Cyberattack frequency is growing and that makes it a real possibility that your business will face a cybersecurity threat sometime soon. Unfortunately, many organizations either don’t take that risk seriously or don’t believe it applies to them, opening themselves up to trouble.
- 60% of SMB owners feel that they will not face any kind of cybersecurity incidents.
- Only 9% of SMB owners ranked cybersecurity as an important success factor
- 18% of SMBs ranked defense against cyberattacks as the least important factor in their success.
- 25% of SMB execs said that they wouldn’t know where to even start with SMB cybersecurity
- Over 65% of senior-level decision-makers said they didn’t believe the businesses for which they’re responsible would ever fall victim to a cyberattack
- One in five companies do not use any endpoint security whatsoever
- One in three small businesses with 50 or fewer employees rely on free or consumer-grade cybersecurity tools for all of their cyber defense
- Only 14% of small businesses rate their ability to mitigate cyber risks and attacks as highly effective
- About 50% of SMBs have no plan in place to handle a cybersecurity incident or cyberattack
- 83% of small businesses haven’t put cash aside for dealing with a cyberattack

Are you ready to slay the Monsters of Cybersecurity? This checklist tells you what you’ll need to succeed! GET CHECKLIST>>
Is Your Budget Ready?
A CNBC /Momentive Small Business Survey expands on that unfortunate conclusion, and the results were no less disturbing. Even with skyrocketing data breach increases, a stunning 56% of the SMB owners surveyed said they are “not very concerned” about being the victim of a cyberattack in the next 12 months, and among those, 24% said they were “not concerned at all.” Many also dismissed the seriousness of today’s biggest risks. The same survey discovered some even more disturbing findings. The SMB owners were generally quite confident (59%) that even if they were hit with a cyberattack, they’d quickly resolve it. Only 37% were “not very confident” and only 11% were “not confident at all.”
Two in five small and medium businesses faced down fearsome monsters like ransomware and business email compromise in a cybersecurity incident last year and most of them weren’t ready to handle the fight. Waiting until the boogeyman arrives on your doorstep is a fast path to disaster – an estimated 60% of businesses shuttered within six months of experiencing a cyberattack. The incredible costs that an unprepared company faces are an enormous contributor to that result – 25% of small business owners in a recent cybersecurity awareness survey didn’t even realize cyberattacks would cost them money.

Go inside the world of hackers and see how it really works with these true tales of cybercrime undercover operations! WATCH NOW>>
Having a Plan Pays
Does every business really need to develop an incident response plan? Yes. An astonishing 94% of executives say their firms have experienced a business-impacting cyber-attack or compromise within the past 12 months. That fact alone should be enough to drive companies to develop a plan for what to do when the worst happens. Many businesses are not prepared for the high cost of falling victim to a cyberattack. If you haven’t planned how your business will handle a cyberattack, you may not have a solid grasp of the costs involved in a response. An estimated 25% of SMB owners stated they had to spend $10,000 or more to resolve one cyberattack. In 2020.
Just creating and drilling an incident response plan includes some amazing benefits for your business. Like a sharp reduction in the number of security incidents that a prepared business faces overall. IBM researchers determined that 39% of organizations with a formal, tested incident response plan experienced an incident, compared to 62% of those who didn’t have a plan. That’s an impressive reduction in risk just from being prepared. If you do have an incident, just having an incident response plan will also save you money. In Ponemon Institute’s “Cost of a Data Breach Report”, researchers determined that having a tested incident response plan can save 35% of the cost of an incident.
Researchers have been banging the drum about the benefits of creating a formal incident response plan for years but the message does not seem to be getting through. For the second year in a row, only 26% of respondents in this year’s IBM Cyber Resilient Organizations Survey reported that their organizations have formal cybersecurity incident response plans that are applied consistently across the entire enterprise. Even with all of the attention that it grabs, only 51% of that tiny fraction of companies reported that their organizations had a specific response plan for ransomware. When specific scenario plans do exist, the top types of attacks for which organizations have response plans for are distributed denial service or DDS (65%), malware (57%) and phishing (51%) incidents.

Is Your Password a Zero or a Hero? Learn the difference and how you can strengthen yours in Build Better Passwords. GET IT>>
Make an Incident Response Plan Now
Making an incident response plan and developing a strategy to reduce an organization’s risk is essential in today’s hair-raising cybersecurity landscape. Fortunately, we can help by giving you the latest intelligence on the cybersecurity nightmares that are targeting businesses every day and common-sense strategies for beating them that will help you sleep at night.
How to Get Started on Creating an Incident Response Plan
Making an incident response plan isn’t as complex as you may think. While there are several popular guides for incident response plans, the most fundamental industry-standard plan uses the framework developed by the National Institute of Standards in Technology (NIST).
The NIST Incident Response Lifecycle contains four steps:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
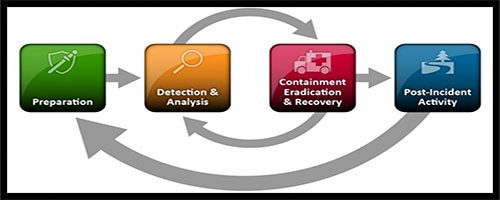
Understanding and adequately accomplishing each step is vital to creating an efficient incident response plan. You can see the agency’s breakdown in the basic NIST Incident Response Planning Guide
In order to carry out your plan, you’ll need the right team. NIST offers an excellent breakdown of the options you might consider for team makeup, why each role is important, and how to choose the right person for the job in their Computer Security Response Planning Guide.
These additional resources also provide excellent examples of an incident response plan.
Carnegie-Mellon University Incident Response Framework
The State of California Template
CISA Example Incident Response Template
NIST Computer Security Incident Handling Guide

Use our Cybersecurity Risk Protection Checklist to find vulnerabilities before the bad guys do! GET IT>>
ID Agent Can Help You Ward Off These Monsters
Secure identity and access management helps ensure that you only let the right ones in. A foundational element of zero-trust security, maintaining tight access control makes it harder for the bad guys to slip in unnoticed to strike your organization even if they have help inside.
Passly is the solution that you’re looking for to make secure identity and access management easy and affordable. Not only does it help maintain compliance with today’s standards, but Passly also ensures that a zero-trust framework is within reach to set every organization up for compliance success in the future.
- Multifactor authentication (MFA) is a requirement for most industries’ compliance standards and CISA compliance standards. According to Microsoft, It’s also 99% effective in preventing password-based cybercrime like using a stolen (or purchased) password and hacking.
- Single sign on makes sure that access controls stay tight by making sure that the right people have access to the right things at the right levels and gives tech staffers an edge when responding to security incidents that can prevent major damage.
- Get quick and easy access to SSO applications and passwords with the ability to automatically fill in those credentials for web logins.
- Automated password resets, secure shared password vaults, seamless integration with over 1,000 business applications and robust remote management capabilities reduce tech staff stress and decrease incident response times.
- Get multiple key security components in one solution at a rate far below the competition, especially when compared to the total cost of products from multiple vendors.
We’re ready to help you take your organization’s password security to the next level with Passly and the strong security solutions in the ID Agent Digital Risk Protection Platform. Don’t take chances with password security for another day. Contact our solutions experts and let’s get started!

Learn how to defeat terrifying cybersecurity monsters to keep systems & data safe in a dark world! READ IT IF YOU DARE!>>