The Week in Breach News: 05/22/24 – 05/28/24

This week: Hacking at a big pharma services provider leads to a data breach for 11 major drug companies, the Mid-Year Cyber Risk Report 2024 just dropped and Vonahi’s report on the industries in which penetration testers found the most dangerous security problems.

What challenges will IT pros face in the second half of 2024? Find out in the Mid-Year Cyber Risk Report. GET IT>>

Cencora
https://www.cyberdaily.au/security/10622-11-us-big-pharma-firms-affected-in-cencora-cyber-attack
Exploit: Hacking
Cencora: Pharmaceutical Services Provider

Risk to Business: 1.401 = Extreme
11 major drug companies have disclosed that they have suffered a data breach as the result of a February 2024 hacking incident at pharma services giant Cencora. The impacted companies include Bayer Corporation, Novartis Pharmaceuticals, Regeneron Pharmaceuticals, AbbVie, Incyte Corporation, Genentech, Sumitomo Pharma America, GlaxoSmithKline Group, Acadia Pharmaceuticals and Endo Pharmaceuticals. The California Attorney General’s Office said in a posting that Cencora had determined in an investigation that ended in April 2024 that patient data that Cencora retained for each of those companies including a patient’s full name, address, health diagnosis, medications and prescription data was accessed by bad actors. Cencora is offering recipients two years of free identity protection and credit monitoring services through Experian.
How It Could Affect Your Customers’ Business: A breach that involves sensitive medical data is an expensive proposition for a business or medical system.
Kaseya to the Rescue: Learn about the growing list of cybersecurity challenges that organizations face in the Kaseya Security Survey Report 2023. DOWNLOAD IT>>
The Government of Albany County, New York
https://therecord.media/albany-county-new-york-government-cybersecurity-incident
Exploit: Hacking
The Government of Albany County, New York – Regional Government

Risk to Business: 1.856 = Severe
Albany County Executive Daniel McCoy has confirmed that the county is experiencing cybersecurity trouble. So far, there hasn’t been a major disruption to county services. However, anyone seeking certificates of residency online will need to call the county Division of Finance, rather than use the county’s online service which is down. No determination has been made about the extent of the breach or if any data was stolen. County officials said that they are working with the U.S. Department of Homeland Security and the Emergency Services Cyber Incident Response Team to investigate the incident.
How It Could Affect Your Customers’ Business: Governments and government agencies have seen an increasing tide of pressure from bad actors that is expected to continue.
Kaseya to the Rescue: Learn how to protect businesses from dark web danger and mitigate cyberattack risk with the insight we share in The IT Professional’s Guide to Dark Web Defense. DOWNLOAD IT>>


Learn how Datto EDR satisfies cyber insurance requirements for endpoint protection & EDR. DOWNLOAD REPORT>>
The City of Wichita, Kansas
Exploit: Ransomware
The City of Wichita, Kansas: Metropolitan Government








Risk to Business: 1.721 = Severe
The city of Wichita, Kansas is beginning the slow climb back to full functionality after a successful ransomware attack by LockBit. The city disclosed last week that law enforcement incident and traffic information was snatched from its computer network between May 3 and 4, 2024. City officials pointed to an unnamed software vulnerability as the bad actors’ entry point. Data stolen in the incident includes peoples’ names, Social Security numbers, driver’s license or state identification card numbers and payment card information. The city warned residents that it will take time for all systems to be restored, including systems used to pay utility bills.
How It Could Affect Your Customers’ Business: It’s critical that every organization conduct regular phishing simulations to mitigate its risk for often email-based cyberattacks like ransomware.
Kaseya to the Rescue:
Sav-Rx
https://www.cyberdaily.au/security/10629-2-8m-affected-in-sav-rx-data-breach
Exploit: Hacking
Sav-Rx: Prescription Management Provider








Risk to Business: 1.803 = Severe
Over 2.8 million people had personal and medical data exposed in a breach at prescription manager Sav-Rx. In a disclosure to the Maine Attorney General, the company noted that in October 2023, bad actors accessed data including patients’ names, dates of birth, email addresses, physical addresses, phone numbers, social security numbers, insurance identification numbers and eligibility data for prescriptions. The company said that it is working with law enforcement in its continuing investigation.
How It Could Affect Your Customers’ Business: Medical data, especially when it includes payment data, is a valuable commodity that bad actors are always looking to snatch.
Kaseya to the Rescue: An endpoint detection and response solution can help businesses stop the spread of cyberattacks fast. This checklist helps you find the right one. DOWNLOAD IT>>
Merrill Lynch, Pierce, Fenner & Smith Inc.
Exploit: Human Error
Merrill Lynch, Pierce, Fenner & Smith Inc.: Recordkeeping Services








Risk to Business: 1.712 = Severe
1,883 Walmart employees who participate in the Walmart 401(k) Retirement Plan were notified last week about a data breach that occurred at recordkeeper Merrill Lynch, Pierce, Fenner & Smith Inc. The company told the impacted Walmart employees that on April 16, a Merrill employee mistakenly disclosed personal information to an unauthorized recipient in an email. The information exposed included the employees’ first names, last names and Social Security numbers. Merrill is providing a complimentary two-year membership in an identity theft protection service eligible for affected individuals.
How it Could Affect Your Customers’ Business: Human error is still the leading cause of a data breach, but frequent employee training helps reduce risk.
Kaseya to the Rescue: Our infographic walks you through exactly how security awareness training prevents the biggest cyber threats that businesses face today. DOWNLOAD IT>>
Trionfo Solutions
https://www.jdsupra.com/legalnews/trionfo-solutions-announces-data-breach-3073267
Exploit: Hacking
Trionfo Solutions: Business Intelligence Software Provider








Risk to Business: 2.376 = Severe
Illinois-based Trionfo Solutions told the Attorney General of Maine that it had experienced a data security incident. The company said that bad actors illegally accessed its systems between December 4, 2023, and December 6, 2023. Breached information varies depending on the individual, but it may include a consumer’s name, address, date of birth, Social Security number, phone number and email address. Trionfo Solutions said that it has sent out data breach letters to anyone who was affected.
How it Could Affect Your Customers’ Business: Bad actors will seek out any opening to exploit, making penetration testing a must-have to close gaps.
Kaseya to the Rescue: Our Penetration Testing Buyer’s Guide walks you through the pentesting process to help you find the right pentesting solution for your needs. GET THE GUIDE>>
TRC Talent Solutions
https://www.jdsupra.com/legalnews/trc-talent-solutions-data-breach-8503470
Exploit: Hacking
TRC Talent Solutions: Staffing Agency








Risk to Business: 1.866 = Severe
TRC Talent Solutions, a Georgia-based staffing company sometimes known as TRC Staffing Services, has disclosed that it suffered a data breach to the Attorney General of Maine. The May 24, 2024, filing said that unauthorized parties gained access to a trove of data between March 25 and April 12, 2024. The intruders stole personal data that TRC was holding including the names and Social Security numbers of job seekers. TRC said that it has sent out data breach letters to anyone who was affected.
How it Could Affect Your Customers’ Business: A staffing company can be a great source for a variety of data making it attractive to the bad guys.
Kaseya to the Rescue: There are a bewildering array of acronyms used for cybersecurity technologies. This infographic breaks down six of them. DOWNLOAD IT>>


See the challenges companies face & how they’re overcoming them in The Kaseya Security Survey Report 2023 DOWNLOAD IT>>


Wales – The Welsh Rugby Union (WRU)
https://www.computing.co.uk/news/4265074/rugby-union-investigates-member-leak
Exploit: Misconfiguration
The Welsh Rugby Union (WRU): Sports Group








Risk to Business: 2.602 = Moderate
The Welsh Rugby Union (WRU) said that it is investigating a data breach that may have exposed nearly 70,000 members’ personal information. The organization pointed to a misconfigured AWS S3 bucket left publicly accessible as the source of the trouble. WRU disclosed that member data including full names, dates of birth, phone numbers, home addresses, email addresses, membership purchase details and the type of membership purchased was stored in that bucket. WRU stressed that no password or payment information has been compromised.
How it Could Affect Your Customers’ Business: Even organizations like sports leagues are potential targets for cybercrime.
Kaseya to the Rescue: This infographic includes 10 handy tips to help you get the most out of your security awareness training solution and run an effective program. GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




vPenTest is now CREST certified
Vonahi’s vPenTest has now become the first and only automated penetration testing solution to achieve CREST certification. CREST is an international not-for-profit membership body representing the global cybersecurity industry. This certification assures industry professionals and buyers that vPenTest stands above the competition, offering superior performance and accuracy. LEARN MORE>>


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


The Mid-Year Cyber Risk Report 2024 is here!
In our Mid-Year Cyber Risk Report, we lay out the biggest cyberthreats on the block in 202 while offering insight into the challenges that IT professionals may grapple with in the second half of this year.
- Explore AI-enabled cybercrime, supply chain risk and zero-day exploits.
- Look at 2024’s trends through the lens of seven impactful cyberattacks.
- Gain insight into the threats we expect to see in the second half of the year.
- Get tips to mitigate these dangerous threats.
Did you miss…Vonahi’s Top 10 Critical Pentest Findings for 2024 report? DOWNLOAD IT>>


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>



Discover the Industries Where Pen Testers Found the Most Dangerous Security Problems
Every day, Managed Service Providers (MSPs) strive to keep their clients’ systems and data safe. However, that has become an increasingly difficult task as cybercriminals refine their Tactics, Techniques and Procedures (TTPs). The evolution of cyber threats means that cyberattacks have been continually growing in sophistication and frequency, and traditional methods of identifying vulnerabilities can’t keep up with the pace of that evolution. After completing over 10,000 automated network penetration tests in 2023, Vonahi has identified the Top 10 critical internal network pentest findings across more than 1,200 organizations – and every information technology professional needs to see the results.
Excerpted in part from Vonahi’s Top 10 Critical Pentest Findings Report for 2024 DOWNLOAD IT>>
Which industries are most at-risk?
As MSPs continue to bolster their clients’ defenses against data theft and cyberattacks like ransomware, savvy cybercriminals have learned that they need to find new methods of penetrating that security. They’re looking for any way inside an organization’s perimeter. However, our research showed that businesses in some industries are more likely to have vulnerability risks than others.
Which industry did pen testers uncover the most problems in when conducting tests? Technology. clocking in at a little over 12%. Investments came in second at about 11%. It’s important to note that investments and finance were considered separate fields in this report, with finance in fourth place at almost eight percent. That’s a total of over 18% for money-moving firms. The banking and financial services sector is traditionally a top target of cyberattacks. However, risk is growing and shifting in every sector as technologies like generative artificial intelligence (AI).
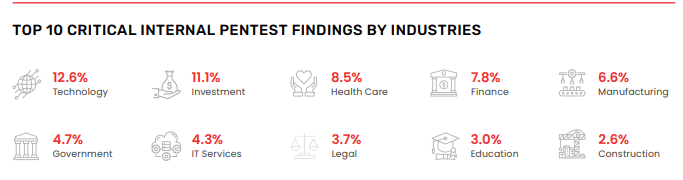

Source: Vonahi Security


Is building an in-house SOC a smart move? Our whitepaper breaks down the costs. READ IT>>
8 reasons why MSPs should invest in automated penetration testing
Enter automated penetration testing—a game-changer for MSPs looking to bolster their security offerings. Here’s why MSPs should seriously consider investing in automated penetration testing.
1. Enhanced Efficiency and Scalability
Manual penetration testing is a time-consuming process that requires significant human resources and expertise. Automated penetration testing, on the other hand, can scan large networks quickly and efficiently. By automating routine tasks, MSPs can free up their skilled professionals to focus on more complex issues. This scalability ensures that even as client bases grow, the quality of security assessments does not diminish.
2. Continuous Monitoring and Real-Time Updates
Cyber threats are constantly evolving, with new vulnerabilities emerging almost daily. Automated penetration testing tools provide continuous monitoring and real-time updates, ensuring that MSPs can detect and respond to threats as they arise. This continuous approach contrasts with the periodic nature of manual testing, offering a more dynamic and proactive security posture.


Learn how to identify and mitigate malicious and accidental insider threats before there’s trouble! GET EBOOK>>
3. Cost-Effective Security Solutions
For many MSPs, budget constraints are a significant concern. Automated penetration testing reduces the need for extensive manual labor, which can be costly. By investing in automation, MSPs can offer more competitive pricing while still delivering comprehensive security services. This cost-effectiveness can be a crucial differentiator in a crowded market.
4. Consistent and Reliable Results
Human error is an inherent risk in any manual process. Automated penetration testing tools are designed to follow strict protocols and procedures, ensuring consistency and reliability in every test. This consistency helps build trust with clients, as they can be confident that their security assessments are thorough and accurate.
5. Rapid Identification and Remediation of Vulnerabilities
One of the primary benefits of automated penetration testing is its speed. These tools can quickly identify vulnerabilities, allowing MSPs to address them before they can be exploited. Rapid detection and remediation are critical in minimizing the potential damage from cyber attacks, protecting clients’ sensitive data and maintaining their trust.
6. Comprehensive Coverage
Automated penetration testing tools can cover a wide range of attack vectors and scenarios that might be missed in manual testing. This comprehensive approach ensures that all potential vulnerabilities are identified, from web application flaws to network configuration issues. For MSPs, this means offering a more robust and all-encompassing security service.
7. Regulatory Compliance and Reporting
Many industries are subject to stringent regulatory requirements regarding cybersecurity. Automated penetration testing tools often include features that help MSPs generate detailed reports and maintain compliance with standards such as PCI-DSS, HIPAA, and GDPR. These tools can streamline the reporting process, ensuring that clients meet their regulatory obligations with minimal hassle.
8. Competitive Advantage
In a competitive marketplace, MSPs need to differentiate themselves. Offering automated penetration testing as part of a comprehensive security package can be a significant selling point. Clients are increasingly aware of the importance of cybersecurity, and those that provide cutting-edge solutions will stand out from the competition.
Elevate Your Security with vPenTest: The Ultimate Automated Network Penetration Testing Solution
vPenTest is the premier, fully automated network penetration testing platform designed to proactively minimize security risks and breaches across your organization’s IT environment. By eliminating the need to source qualified network penetration testers, vPenTest delivers high-quality results that clearly outline identified vulnerabilities, assess their risks, and provide strategic and technical remediation guidance. Additionally, it enhances your compliance management capabilities effortlessly. The benefits of vPenTest are unbeatable
Comprehensive assessments made easy
With vPenTest, conduct both internal and external network penetration tests seamlessly, ensuring every potential entry point in your network infrastructure is meticulously examined.
Real-world simulation
Experience real-world cyber threat simulations with vPenTest, gaining invaluable insights into your security posture and preparedness against malicious actors.
Timely and actionable reporting
Post-testing, vPenTest provides detailed, yet easy-to-understand reports, highlighting vulnerabilities, their potential impacts, and recommended mitigation actions, ensuring you’re always a step ahead.
Ongoing penetration testing
Stay proactive with vPenTest’s affordable monthly testing intervals, maintaining a robust security posture that swiftly adapts to emerging threats.
Efficient incident response
By identifying vulnerabilities proactively, vPenTest ensures you’re better prepared to respond to potential security incidents efficiently and effectively.
Compliance alignment
vPenTest aligns seamlessly with regulatory compliance requirements such as SOC2, PCI DSS, HIPAA, ISO 27001, and cyber insurance mandates, simplifying your compliance management process.
Transform your security approach with vPenTest—your trusted partner in automated network penetration testing. Ensure comprehensive, real-time protection and compliance, all while streamlining your security operations. BOOK A DEMO NOW>>


Balancing Cybersecurity: Building Your Own SOC vs Partnering With a Managed SOC
June 5, 2024 I 1 PM ET / 10 AM PT
Choosing between establishing an in-house security operations center (SOC) or opting for a Managed SOC is an important step when building your cybersecurity strategy. The insight you gain in this webinar can help you successfully navigate that complex decision-making process. You’ll learn about:
- The investment and resources needed for both options
- The benefits and challenges of each option
- The experiences of other IT professionals in real-world case studies.
June 11-13: Kaseya DattoCon Europe (Dublin) REGISTER NOW>>
June 19: The Top Cyberattack Trends of 2024 REGISTER NOW>>
June 18: Kaseya+Datto Connect Local Toronto (Security and Compliance Series) REGISTER NOW>>
October 28 – 30: Kaseya DattoCon (Miami) REGISTER NOW>>
November 12 – 14: Kaseya DattoCon APAC (Sydney) REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!