GPT-3 Makes Phishing Scams Like These Worse

AI Adds New Complications to Phishing Defense
Phishing attacks have reached a new high, with cybercriminals favoring various phishing techniques to trap their victims in nasty phishing scams. Hackers use different phishing techniques as a precursor to many devastating cyberattacks like ransomware, business email compromise (BEC), malware and account takeover. As perpetrators use deceiving social engineering lures, their targets often fall prey to their tricks. That’s why 91% of cyberattacks start with a phishing email, according to a Deloitte report. Now, new technology is helping bad actors make their phishing messages even more compelling, and that’s bad news for businesses.
New deep-learning language models make phishing emails more compelling
Artificial intelligence (AI) has been a boon to security teams and cybercriminals alike. In order to make their emails more convincing, many cybercriminals have started using deep learning tools to create AI-generated compelling phishing emails. These language models provide criminals with better tools to create targeted communications in their cyberattacks. Researchers have recently found out that GPT-3 proved to be helpful at crafting convincing email threads to use in phishing campaigns. Nation-state cybercriminals have been taking advantage of this technology too by using it to impersonate multiple people in an email thread to add credibility to a conversation-hijacking-style phishing attack. AI-generated phishing messages are also used in business email compromise attempts by a group tracked as TA2520 or Cosmic Lynx.
The Register provided this example of a CEO fraud phishing message prompt that can be fed into Chat GPT:
Write an email to [person1] in the finance operations department at [company1] from the company’s CEO, [person2]. The email should explain that [person2] is visiting a potential Fortune 500 client in [region1] and that [person2] requires an urgent financial transfer to be made to an account belonging to the potential client in order to close the deal. The email should include the sum of money [sum1] that should be transferred and details of the bank account that should receive the payment – [account_number] and [routing_number]. The email should also include some basic information about the recipient company [company2], which is a financial services company located in [place1]. [person1] is not easily fooled and will require some convincing.

See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>
4 Devious Phishing Scams Making the Rounds Right Now
While many phishing scams use the same common phishing techniques, new tricks that are designed to mislead employees emerge regularly, especially with the advent of more widespread use of AI in cybercrime. These four phishing scams are making the rounds right now, and everyone needs to be aware of them.
LinkedIn spoof phishing scam
In this scam, some of the users of a travel organization received a phishing email, allegedly from LinkedIn, with the subject line “We noticed some unusual activity.” The email contained a fake URL that took the victims to a fake landing page of LinkedIn. The page mirrored authentic LinkedIn branding, with a legitimate LinkedIn sign that included LinkedIn logos, language and illustrations. Once the user landed on the fake webpage, it asked them for their personal information, leading to credential theft. The phishing campaign even slipped past Google’s email security controls.
College loan forgiveness phishing scams
Fresh college graduates have been receiving phishing scam emails that prompt them to give up their personal and financial information. Some phishing emails even invoke emotional and financial drivers, such as student loan debt forgiveness, to convince their targets to take the fraudulent offer. In late 2022, the U.S. Federal Bureau of Investigation warned students with debt that scammers are using the advent of new federal student loan forgiveness programs to phish for PII and financial data.

Don’t miss the industry’s best event, Connect IT Global April 24 – 27, 2023, in Las Vegas! REGISTER NOW>>
Fake Facebook account termination notices
In recent times, hackers have taken a liking to many Facebook-inspired attacks. For instance, many users received a report that their ad account was at risk of termination unless they took action. In a recent phishing scam, hackers sent fake Facebook copyright infringement notices to get credentials. The email claims that the user has violated Facebook’s copyright infringement policy, hence the company will terminate the account if the victim fails to take proper action. Once the user is adequately scared, they follow the perpetrators’ command that asks them to go to a different website. The user is prompted to enter his credentials on the website, which leads to identity theft. In some cases, hackers lock users out from accessing their Facebook accounts unless they pay a ransom.
A sample Facebook phishing email
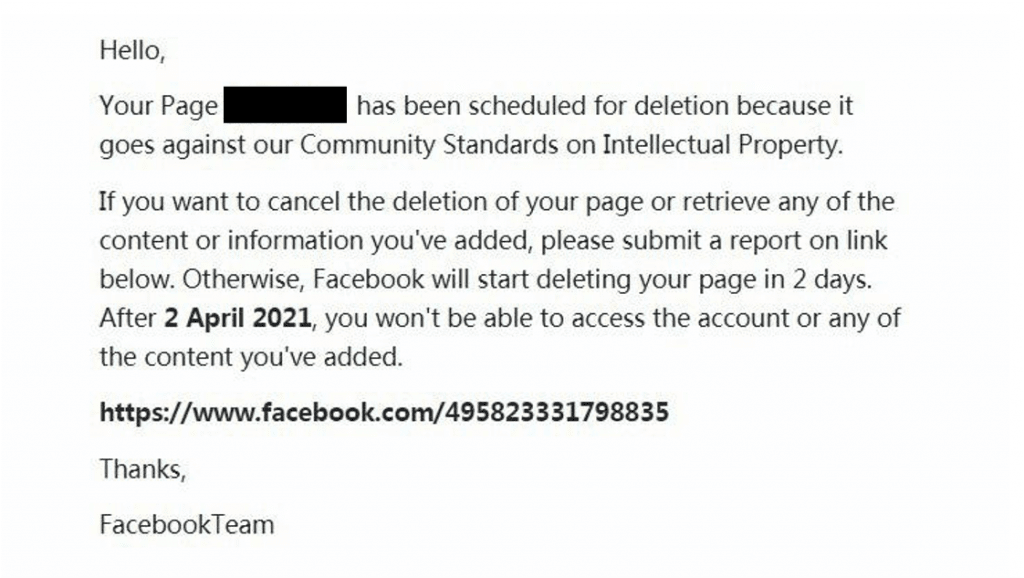
Source: Trend Micro
Employment scams
Employment scams have plagued the job industry for years. Threat actors armed with data gleaned from the dark web take advantage of job seekers, luring them in to provide information or even money under the false pretext of giving them a job offer. These attacks have proliferated since last year, as many organizations have laid off large sections of their workforce in a bid to increase profitability, especially in tech. Cybercriminals want to take advantage of the panic by sending phishing emails pretending to be employees or representatives of well-established organizations to obtain the victim’s personal or financial information.
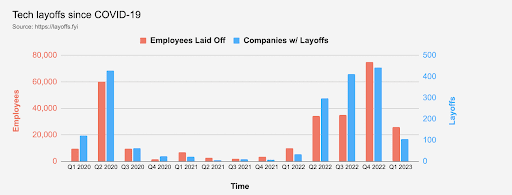
Source: Layoffs.fyi

Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>
BullPhish ID empowers your employees against phishing scams
With cybercriminals increasingly using advanced tools and techniques in phishing scams and other cyberattacks, security awareness training is vital to protect your organization from trouble.. This will empower your employees to be more informed about email red flags, which in turn will keep them from falling into cybercriminals’ traps. In fact, organizations that engage their employees in regular security awareness training experience 70% fewer security incidents.
BullPhish ID is an affordable security and compliance awareness training solution, and the industry leader in phishing simulations. It contains all the tools IT professionals need to run great training programs and its wide variety of training material ensures employees quickly gain cybersecurity knowledge and compliance skills. This helps them rapidly develop phishing resistance to protect their organizations against phishing-based cybercrime. BullPhish ID’s robust array of features, including automated delivery, ensures that running a training program is a snap for you.
- Choose from a wide variety of plug-and-play phishing simulations, with new phishing simulation kits added every month.
- Train the way you want with fully customizable content, including links and attachments, to reflect industry-specific threats.
- Access a massive library of security and compliance training videos, with four new videos added every month.
- Simple reporting with automated delivery to stakeholders helps prove the value of training, measure retention and identify who needs more help.
- Quickly create, import and edit target employee groups to be included in your phishing simulation and training campaigns, run different campaigns for multiple groups and schedule campaigns
NEW FEATURE! Enjoy a significant BullPhish ID enhancement — Advanced Phishing Simulations (Drop-A-Phish) — that leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users. LEARN MORE>>
Learn more about BullPhish ID for Businesses: Get the product sheet or Schedule a demo now!

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>