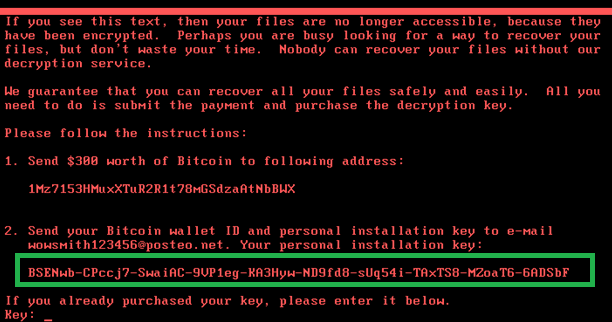
NotPetya – a Threat to Supply Chains
Ukraine is a nation under digital siege. Over the past few months, it has suffered through four widespread infrastructure attacks, with the Russian government being suspected as the driving force behind the attacks — although to date, there’s no clear evidence of this.
Read More







