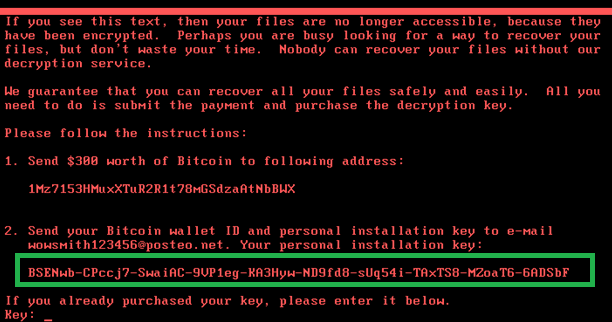
OneLogin – When Password Storing Goes Wrong
OneLogin, a company that provides single sign-on capabilities to safely store passwords of over 23 million users including 2,000 businesses, has suffered a compromise that included the ability to decrypt customer data. In a recent blog, the company revealed that an attack occurred May 31st at 2 am and was identified by a staff member around 9 am. Through that attack, sensitive information such as user information: passwords and emails, various keys from companies and login credentials for a slew of cloud applications were potentially compromised. In the OneLogin blog post, it was stated that they “…cannot rule out the possibility that the threat actor also obtained the ability to decrypt data.” And according to the email sent out after the breach, customers were instructed on steps they should take to proactively prepare themselves. They were advised to force a OneLogin Directory Password Reset for end users, update credentials on 3rd party apps for provisioning and to do numerous other things. The email also included further updates and information.
Read More