Businesses Face Growing Cyberattack Risk from Dark Web Exposure

See What Exposed Credentials & Data Can Do to a Business
Gone are the days when the dark web conjured up images of hoodie-clad hackers who work on behalf of sinister organizations to coordinate trades in weapons or narcotics. The dark web has emerged as the seedy underbelly of the internet where cybercriminals can buy stolen critical business data, user credentials and the tools that facilitate cybercrime. The resources available on the dark web help cybercriminals plan operations and conduct attacks against businesses. As information floods into dark web markets and data dumps every day, the risk that a business cloud fall into trouble because o dark web exposure grows every day.

What worries security pros? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>
The world’s third-largest economy is booming
The dark web is replete with information that can damage businesses like stolen critical business information, ransomware, malware and hacking services. An estimated 60% of the information available on the dark web could potentially harm enterprises. Those commodities are commonly traded on dark web message boards. It’s the world’s third-largest economy, and it is growing fast. Cybersecurity Ventures estimates that the dark web will inflict about $6 trillion in damages worldwide in 2021, placing the dark web economy just behind the United States and China, the top two world economies.
Business data and credentials are major revenue drivers and valuable resources for cybercriminals. Those commodities are sold, traded and harvested in dark web markets every day. How does information like that make its way to the dark web? Through a variety of pathways, including:
- Data hack: Hackers take advantage of weak network security to enter into an organization’s network and rob them of their precious data.
- Phishing: Phishing has become the most used and dreaded attack vector through which threat actors steal business data. They send emails to the victims, purporting to be from a trusted source and attach a malicious file, such as a Word or Excel document referred to as a maldoc, a .JS file or a portable executable (PE) file. Phishing attacks aim to steal sensitive data like credit card and login information or install malware on the victim’s machine.
- Malware: Hackers inject malware on some legitimate websites that their targets usually frequent. Once the user clicks on the malware, cybercriminals take control of their systems to steal their user credentials and other critical information.
- Keylogging: It is the action of recording the keystrokes of an unaware user. Cybercriminals use keystroke recorder programs to retrieve the data. Keylogging is often used for stealing passwords and other confidential information, which is then sold on the dark web for monetary gain.

Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>
The market for data is thriving
According to the 2022 Dark Web Product Price Index, the dark web data market has grown significantly in both the volume of data that is added, sold or traded and the variety of information that is available. It’s also grown more competitive. Many cybercriminals are offering discounts and other specials to lure potential clients these days. The most expensive item included in the data set is premium malware, which costs about $5,500 per 1,000 installs, However, bad actors can buy stolen data by spending less than $1, and sometimes it’s even free. Other data sets in the report include PayPal account details, Netflix logins and stolen credit card details (complete with a CVV) that are all available for less than $20.
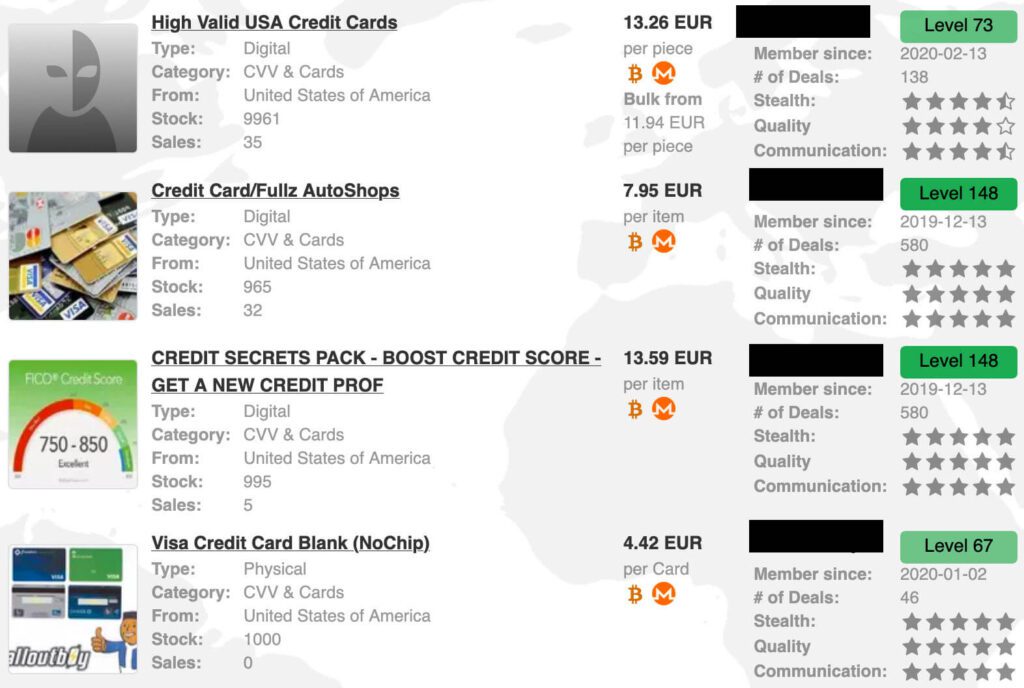
A screenshot of stolen credit cards sold on the dark web (Source: Privacy Affairs)

Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>
Credential exposure is a ticking time bomb
Credentials are the keys to the kingdom for businesses and huge quantities of them are floating around on the dark web. At this moment, more than 24.6 billion complete sets of usernames and passwords are currently in circulation on the dark web, which is four full sets of credentials for every person on Earth. Many of those credentials made their way to the dark web in the same way that other information does. Most commonly, credentials end up in dark web markets after they’re stolen in a data breach.
Of course, it doesn’t help that people are notoriously bad at choosing complex passwords. Most people use some type of mnemonic to make it easy for them to remember a password. In a study, researchers discovered that over 59% of American employees use a person’s or a relative’s name or birthday as their password. We’re also guilty of using our pet’s names, our favorite sports team and other insecure, easy-to-guess passwords.
Another path to credential exposure is more unpleasant for businesses to consider: malicious insiders. Disgruntled employees can easily sell their credentials, and other data about their company like lists of credentials, on the dark web for a profit. Malicious insider actions like selling credentials result in an estimated 25% of data breaches. The higher level of privilege a credential has, the more money they’ll make. An average legitimate corporate network credential sells for around $3,000, and an average legitimate privileged network credential can go for as much as $120,000.

Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>
The availability of data and credentials on the dark web is a disaster for businesses
Businesses are the primary targets of today’s nastiest and most lucrative cyberattacks. IBM named stolen or compromised credentials as the top cause of a data breach in a 2022 report. The sophisticated ransomware and other malware readily available also helps cybercriminals hold businesses hostage and make them dance to their tunes until the business pays up. Information about people and businesses plays a major role in the distribution of ransomware. Ransomware and malware are most commonly distributed through spear phishing, and cybercriminals use any data they can find about their target on the dark web to make their malicious message seem authentic and compelling to their victims.
Even without direct interaction with the dark web, organizations must be aware of their exposure to it. But too many companies don’t take cybersecurity risk seriously. Unfortunately, in a recent survey, over 36% of board and C-suite members said that they viewed cybersecurity as solely a compliance matter. Only 17% of them even listed cybersecurity as a priority. Plus, the relationship between non-technical executives and Chief Information Security Officers (CISOs) or their equivalent is not always open. Even more troubling, only about one-fifth (20%) of CISOs surveyed agreed that they have solid partnerships with business leaders, citing cybersecurity’s complexity as a major blocker.
It is hard to prevent dark web infiltration but being aware and staying vigilant against it can lessen the damage. Being prepared before the worst happens with an incident response plan is important to ensure a business’s survival by minimizing damage and shortening the time it takes to get a victimized business back on its feet. However, nothing beats preventing that attack from happening in the first place. One of the most effective ways to do that is by engaging in dark web monitoring to find a company’s compromised credentials on the dark web and neutralize them before the bad guys have a chance to use them against that company.

Get a step-by-step guide to building an effective security and phishing awareness training program. GET GUIDE>>
Find and Fix Credential Vulnerabilities with Dark Web ID
Dark Web ID is your secret weapon for continuous protection from dark web threats.
Dark Web ID watches every corner of the dark web, including more than 640,000 botnets, hidden chat rooms, unindexed sites, private websites, peer-to-peer (P2P) networks, internet relay chat (IRC) channels, social media platforms, black market sites, hacker forums and all of the places that cybercriminals do business 24/7/365. If one of a company’s credentials pops up, Dark Web ID alerts that company to credential compromise danger immediately.
The dark web search add-on finds every compromised credential an organization has out there in minutes, enabling IT professionals to eliminate those vulnerabilities fast. Plus, other add-ons enable businesses to monitor domains, executive personal email accounts, supplier domains and more!
Get your defenses ready for a new onslaught of password-related cybercrime risk. Contact our solutions experts today for a personalized demo to see how the ID Agent Risk Protection Platform can benefit your business.

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>