Automation Makes Credential Stuffing Nastier Than Ever

Cybercriminals Are Bringing the Pain to Retailers with Credential Stuffing Bots
Automation has revolutionized cybersecurity. All types of organizations use automation to perform a slew of repeated and mundane tasks in seconds with utmost efficiency without any manual invention. That includes cybercriminal organizations. Unfortunately for businesses, automation has facilitated the resurgence and upward growth of a devastating classic cyberattack technique that’s been updated for the modern era: credential stuffing.

What worries security pros? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>
Compromised credentials fuel attacks
Businesses and personnel use hundreds of applications and websites for a variety of digital services. Almost all these websites and apps use passwords for user authentication. Users often tend to reuse the same passwords across multiple online services to manage these online accounts. More than 60% of people habitually reuse passwords across multiple sites and applications. While password reuse might be a convenient way for them to juggle through many online accounts, it has made them attractive targets for cybercriminals, who often rightly assume that passwords stolen from one company may provide the keys to a host of other accounts.
Credential stuffing is a type of cyberattack where threat actors make repeated attempts to log in to a user’s online accounts using stolen usernames and passwords. Sometimes those credentials have been stolen in a previous breach. Cybercriminals may also purchase files of credentials or harvest them from dark web data dumps. However they do it, cybercriminals tap into users’ habit of using the same password for multiple accounts and use it to harm businesses through credential stuffing. Credential stuffing is an especially dangerous problem for retailers. Attackers used leaked credentials more than 90% of the time in credential stuffing attacks targeting retailers, compared to just under 70% of the time in other industries.

Learn to identify and mitigate fast-growing supply chain risk with this eBook. DOWNLOAD IT>>
Credential stuffing has leveled up
There are plenty of password and username pairs for cybercriminals to deluge businesses with in the course of a credential stuffing attack available right now. According to a survey, more than 15 billion stolen credentials are currently circulating on the dark web, and that number grows yearly. Automation has made the process of credential stuffing easier than ever for the bad guys. After getting their hands on user credentials, attackers typically leverage software or other automation tools like bots that are capable of transmitting a sustained barrage of login attempts simultaneously without human intervention. A recent study on retail cybersecurity challenges showed that nearly one-quarter of the traffic on retail websites (23%) was attributed specifically to malicious bots. Once the bad actors deploy their bots, they just have to monitor the operation to see which one unlocks the door and gives them access to a user’s account.
How does credential stuffing work?
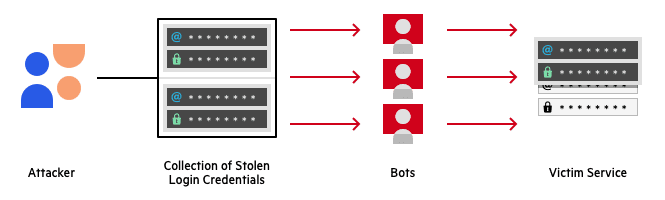
Source: Imperva

Finding the fix for your security & compliance training challenges is easy with our buyer’s guide! GET YOUR GUIDE>>
One compromised credential brings serious consequences
Once cybercriminals have access to a user account, they can view the account holder’s personal information and leverage it in many damaging ways. Bad actors can use it to launch successful social engineering attacks, sell that information on the dark web or make fraudulent transactions if they find financial information. Sometimes, they perform account takeovers on the cracked accounts and use them in business email compromise schemes. The technique is the prime culprit in one-quarter of data breaches.
Although most login attempts in a credential stuffing attack fail, a single attack can yield thousands of compromised accounts due to the sheer volume of attempts. Automation has enabled bad actors to send more attempts than ever before at a target over a very short period, and with the high likelihood that someone has reused a compromised credential, there’s a very high chance that the bad guys will get a hit. The aftermath of a credential stuffing attack can be gauged from the Ponemon Institute’s Cost of Credential Stuffing report, which concluded that businesses lose an average of $6 million per year to credential stuffing in the form of application downtime, lost customers and increased IT costs.

Get 10 tips to help you build a strong security culture & reduce your risk of cybersecurity trouble! GET INFOGRAPHIC>>
3 defensive tips to mitigate credential stuffing risk
Due to the prevalence of credential stuffing attacks, businesses must prepare for an eventuality where such an attack can come knocking down their doors someday. An estimated 81% of data breaches are due to poor password security. Therefore, every company that maintains online customer accounts must take action to ensure that they’re making all the right moves to mount an effective defense against credential stuffing cyberattacks.
- One of the most effective safeguards for preventing credential stuffing attacks is multi-factor authentication (MFA). It ensures that a user presents two or more types of credentials when logging in to their account. While most attackers have access to a stolen password, it is improbable that they will have access to other credential types. Microsoft says that 99.9% of cyberattacks can be stopped with multifactor authentication.
- Regular, comprehensive security awareness training is a stepping-stone for organizations in blocking a credential stuffing attack by cultivating their employees’ levels of security awareness. Employees will make better password-related choices and practice better password hygiene if they understand why it matters. Companies can quickly and affordably educate their employees on how malicious actors can leverage password reuse as part of a credential stuffing campaign. Training also helps them learn the importance of keeping secure, unique passwords for all of their online accounts in order to mitigate the risk of credential stuffing.
- Compromised credentials are fodder for launching credential stuffing attacks. Therefore, monitoring the dark web for leaked or stolen information such as compromised credentials is an essential way to reduce the risk of a credential stuffing attack getting through on a business. Credentials are the top type of information stolen in data breaches worldwide.

Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>
These 2 solutions prevent credential stuffing trouble
Putting robust protection in place against credential stuffing attacks isn’t hard to do or expensive. The ID Agent has the solutions businesses need to stay safe without breaking the bank.
BullPhish ID can efficiently train an organization’s employees against various cyberattacks, including credential stuffing attacks and many other phishing attacks. Select your training videos in 8 languages from a big library. Plus, choose from a wide variety of plug-and-play phishing simulations, with new phishing simulation kits added every month.
Dark Web ID monitors the darkest alleys of the dark web 24/7/365 to check for any credential compromise. Upon finding any compromise, it instantly alerts the concerned authorities, enabling companies to stay a step ahead of cybercriminals.
Contact the solutions experts at ID Agent today to learn more about how the ID Agent digital risk protection platform can enable you to secure your business and your customers against credential stuffing attacks.

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>