3 Trends Shaping Cybersecurity in 2024

The cybersecurity world never slows down, constantly evolving to serve up new risks and novel cyberattacks every day. Keeping track of all of these developments can be a challenge, which is why we’re here to help. The Midyear Cyber-Risk Report 2024 is your essential guide to understanding this year’s pivotal cyber-risk trends. In this edition, we delve into the elements shaping cybersecurity in 2024. Plus, we’ll explore three notable risks that information technology professionals must grapple with to secure business systems and data.
Where did we start?
It’s important to understand where we started at the turn of the year to gain a clear picture of the issues IT professionals face in 2024. In the Kaseya Security Survey Report 2023, we asked IT professionals about their cybersecurity experiences and challenges, and here’s what they had to say.

Source: Mid-Year Cyber Risk Report 2024
Data compromises are at an all-time high
We’ve seen a concerning rise in the number of publicly reported data breaches. The U.S. hit a record high of 3,205 data breaches in 2023 — a 78% increase from the previous year — and it doesn’t seem to be slowing down. In the first quarter of 2024 alone, there were 841 reported breaches, up 90% from the same period in 2023. These figures highlight the critical importance for businesses to keep their cybersecurity strong to protect against data theft.
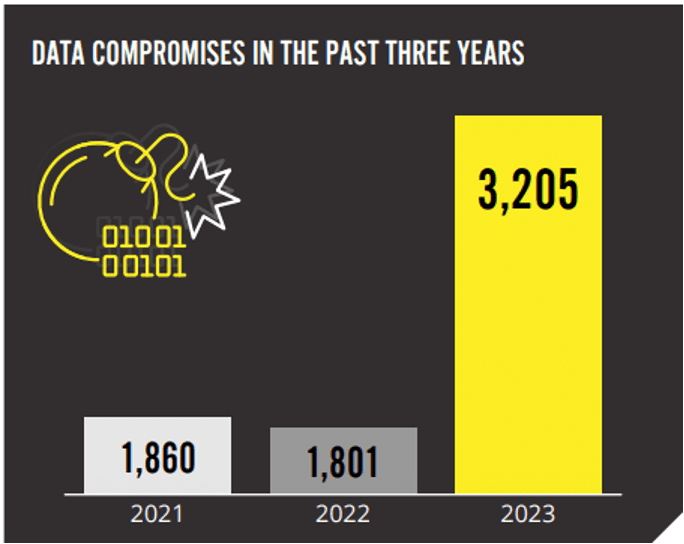
Source: Mid-Year Cyber Risk Report 2024
1. Most IT pros expect their organization to be hit by ransomware
Ransomware remains a significant and ongoing danger to businesses everywhere. Every day, cybercriminals find new ways to use cutting-edge technology, including generative AI, to create new and more sophisticated ransomware and malware. Alarmingly, the majority of the people we surveyed anticipate their organization will face a ransomware attack this year. And they’re probably right — 1,048 ransomware attacks were recorded in Q1 2024, up 73% over the same period in 2023.
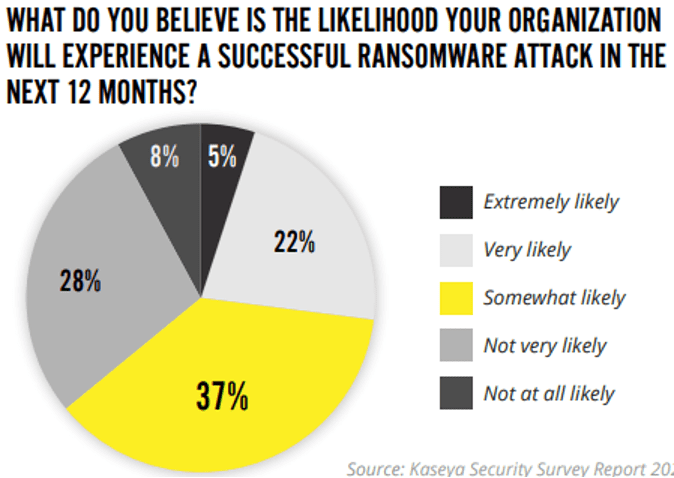
Source: Mid-Year Cyber Risk Report 2024

Learn to defend against today’s sophisticated email-based cyberattacks DOWNLOAD EBOOK>>
2. Zero-day exploits soar
A zero-day attack, which is a cyberattack that exploits previously undiscovered vulnerabilities, is a term that we’re hearing more frequently. In 2023, Google observed 97 zero-day vulnerabilities exploited in the wild. That’s over 50% more than in 2022, when 60 were reported. Several factors have contributed to this surge, including:
- An increasingly interconnected business world as traffic increases between organizations and specialized service providers.
- Cybercriminals searching for new avenues of attack as businesses harden their security.
- Slipshod maintenance and patching by overworked IT teams.
- Modern software development practices that tend to result in common vulnerabilities.
- Patch development focused on temporary mitigations rather than underlying causes.

Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>
3. Supply chain danger is growing
Supply chain cyberattacks hit the headlines in 2023. In the U.S., these attacks affected 2,769 entities — the highest since 2017. Sadly, 61% of the people we surveyed shared that their organization faced a cyberattack via their supply chain or a third-party service provider last year. This trend is on the rise, emphasizing the need for businesses to beef up their defenses in 2024. Experts estimate that 45% of global organizations will experience a supply-chain-related cyberattack by 2025.
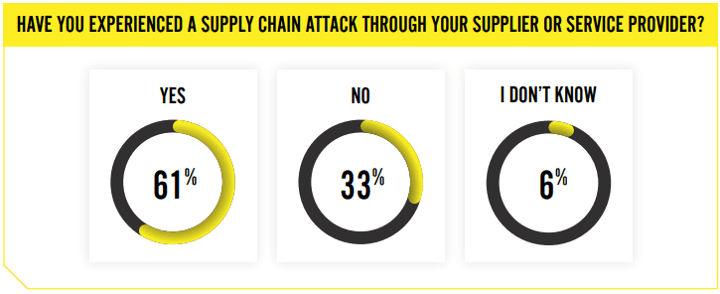
Source: Mid-Year Cyber Risk Report 2024

Learn more about growing supply chain risk for businesses and how to mitigate it in a fresh eBook. DOWNLOAD IT>>
Kaseya’s Security Suite helps businesses mitigate all types of cyber-risk affordably
Kaseya’s Security Suite has the tools that MSPs and IT professionals need to mitigate cyber-risk effectively and affordably with automations and AI-driven features that make IT professionals’ lives easier.
BullPhish ID: This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID: Our award-winning dark web monitoring solution is the channel leader for good reason. It provides the greatest amount of protection around with 24/7/365 human- and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus: Graphus is a cutting-edge, automated phishing defense solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone solution or supercharges your Microsoft 365 and Google Workspace email security.
RocketCyber Managed SOC: Our managed detection and response (MDR) solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR: Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Datto AV: Safeguard businesses effortlessly against sophisticated cyberthreats, including zero-days and ransomware, with AI-driven, next-generation antivirus protection that is over 99% effective, far surpassing the industry average.
Vonahi Penetration Testing: How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.
See how our Security Suite can be put to work for you with a personalized demo.
- Book a demo of BullPhish ID, Dark Web ID, RocketCyber Managed SOC and Graphus. BOOK IT>>
- Book a demo of vPenTest BOOK IT>>
- Book a demo of Datto AV and Datto EDR BOOK IT>>