The Week in Breach News: 06/05/24 – 06/11/24

This week: Another big data breach has something in common with other recent large breaches, nation-state hacking in Germany, seven reasons why IT professionals choose Datto EDR and the top three findings from over 10k penetration tests.

What challenges will IT pros face in the second half of 2024? Find out in the Mid-Year Cyber Risk Report. GET IT>>

Palomar Health Medical Group
Exploit: Hacking
Palomar Health Medical Group: Healthcare Provider

Risk to Business: 2.201 = Severe
Palomar Health Medical Group continues to operate without fully functional systems after a cyberattack knocked it offline. The medical group’s hospitals in Escondido and Poway are not affected, but representatives said in a statement that the attack hit its outpatient facilities, including its Graybill medical offices, limiting their operations. The attack was discovered on May 5, 2024. There is no anticipated timeline for the resumption of full operations.
How It Could Affect Your Customers’ Business: Healthcare centers must be careful to implement robust security because they are frequent targets for cybercriminal activity, creating public health risk.
Kaseya to the Rescue: Learn about the growing list of cybersecurity challenges that organizations face in the Kaseya Security Survey Report 2023. DOWNLOAD IT>>


Germany – Christian Democratic Union (CDU)
https://therecord.media/germany-opposition-party-cyberattack-europe
Exploit: Hacking (Nation-State)
Christian Democratic Union (CDU): Political Party





Risk to Business: 1.856 = Severe
Germany’s major opposition party, the Christian Democratic Union (CDU), announced that it has experienced a large-scale cyberattack, and they suspect that Russia-aligned threat actors are involved. The attack led the party to take down and isolate parts of its IT infrastructure as a precaution. Officials said that law enforcement is investigating. This incident, occurring just before the European Parliament elections, follows a similar attack on the SPD attributed to Russian state-controlled hackers.
How It Could Affect Your Customers’ Business: Governments and government agencies have seen an increasing tide of pressure from bad actors that is expected to continue.
Kaseya to the Rescue: Learn how to protect businesses from dark web danger and mitigate cyberattack risk with the insight we share in The IT Professional’s Guide to Dark Web Defense. DOWNLOAD IT>>
France – Decathlon
https://cybersecuritynews.com/threats-claimimg-breach/
Exploit: Ransomware
Decathlon: Sporting Goods Retailer





Risk to Business: 1.721 = Moderate
Threat actors 888 claim to have stolen a database linked to France-based sporting goods retailer Decathlon. The company confirmed a data security incident involving email addresses of its Spanish employees, discovered on May 27 by its cybersecurity team in Spain. The data originated from a third-party application, and no passwords or customer data were affected.
How It Could Affect Your Customers’ Business: It’s critical that every organization conduct regular phishing simulations to mitigate its risk for often email-based cyberattacks like ransomware.
Kaseya to the Rescue: Learn about the factors that have shaped cybersecurity in 2024 and be ready for what’s next with the knowledge you’ll gain from our Midyear Cyber-risk Report 2024. GET REPORT>>


Every business faces insider risk, from employee mistakes to malicious acts. Learn how to mitigate it. DOWNLOAD EBOOK>>
The Netherlands – Heineken
Exploit: Hacking
Heineken: Brewer





Risk to Business: 2.803 = Moderate
Cybercrime group 888 claims to have exfiltrated the data of 8,174 Heineken employees. The group said that the data belongs to employees across a number of countries, including an employee’s identification scans, full names, email addresses, company roles and more. The threat actors posted a sample of the data, which shows the details of 10 users from countries including Brazil, Nigeria, Indonesia and the UK.
How It Could Affect Your Customers’ Business: A company’s employee data is just as valuable and attractive to cybercriminals as its customer data may be.
Kaseya to the Rescue: An endpoint detection and response solution can help businesses stop the spread of cyberattacks fast. This checklist helps you find the right one. DOWNLOAD IT>>
UK – LivaNova
https://cybernews.com/news/livanova-ransomware-attack
Exploit: Ransomware
LivaNova: Medical Device Maker





Risk to Business: 1.712 = Severe
UK-based medical device manufacturer LivaNova has informed affected individuals that it fell victim to a ransomware attack that led to the exposure of the personal data of current and former employees. Data exposed in the attack includes an employee’s name, telephone number, email, address, Social Security or national identification number, date of birth, financial account information, health insurance information, online credentials and work-related information, such as employee ID, compensation, disability status and evaluations.
How it Could Affect Your Customers’ Business: This treasure trove of information contains details like identification numbers that help facilitate identity theft.
Kaseya to the Rescue: Our infographic walks you through exactly how security awareness training prevents the biggest cyber threats that businesses face today. DOWNLOAD IT>>


Vietnam – Vietnam Post
Exploit: Ransomware
Vietnam Post: Postal Service





Risk to Business: 2.376 = Severe
Vietnam Post said its IT systems have been taken down by a ransomware attack. Officials say the attack happened at around 3 a.m. on June 6, directly impacting activities related to postal delivery. The Vietnam Post’s website and application were inaccessible starting Tuesday morning. Officials stressed that finance postal, public administration and good distribution services are still operating normally. The Vietnam Post said it is working with authorities and its partners to resolve the issues as soon as possible.
How it Could Affect Your Customers’ Business: Disrupting a country’s postal service with a cyberattack could cause a widespread ripple effect that impacts many businesses.
Kaseya to the Rescue: Our Penetration Testing Buyer’s Guide walks you through the pentesting process to help you find the right pentesting solution for your needs. GET THE GUIDE>>


Australia – Ticketek Australia
Exploit: Supply Chain Data Breach
Ticketek Australia: Ticket Seller





Risk to Business: 2.866 = Moderate
Ticketek Australia has informed customers that sensitive stored on a cloud-based platform by a global third-party supplier had been exposed in a data breach at a third-party data storage provider. The company said that customer names, dates of birth and email addresses may have been exposed in the incident. This breach, as well as the recent Ticketmaster and Santander Bank breaches all appear to be related to the cloud data platform Snowflake. However, the platform claims that the breach was caused by its customers’ poor security procedures. The story is still developing.
How it Could Affect Your Customers’ Business: Supply chain and third-party risk is a constant menace for organizations that they must take seriously.
Kaseya to the Rescue: There are a bewildering array of acronyms used for cybersecurity technologies. This infographic breaks down six of them. DOWNLOAD IT>>
New Zealand – Smith & Caughey’s
Exploit: Ransomware
Smith & Caughey’s: Retailer





Risk to Business: 2.602 = Moderate
Auckland department store Smith & Caughey’s has fallen victim to a cyberattack, on the same day it announced it proposed to close in early 2025, after 144 years in business. A store executive said that the store’s server and retail operations systems have been crypto-locked, likely the result of a ransomware infection. The official stated that the attack has impacted the store’s ability to communicate with staff, customers, suppliers and other critical stakeholders.
How it Could Affect Your Customers’ Business: A ransomware attack can be enough to knock a teetering business out, making prevention mission-critical.
Kaseya to the Rescue: This infographic includes 10 handy tips to help you get the most out of your security awareness training solution and run an effective program. GET INFOGRAPHIC>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Find out about five of today’s biggest dark web threats to businesses in this infographic. DOWNLOAD IT>>




Spruce up your training with these two refreshed training modules
We’ve refreshed two of our most popular training modules in BullPhish ID to ensure that they deliver training that covers the latest cyber threats.
- What is an insider threat? Learn about the danger of threats that come from within an organization.
- What is account takeover (ATO)? Learn how to prevent intruders from stealing your credentials and taking over your accounts.
Learn more about these training modules and other innovations in the BullPhish ID Release Notes. LEARN MORE>>


How much is data really worth on the dark web? Find out in The IT Professionals Guide to the Dark Web! GET EBOOK>>


New infographic: 7 Reasons Why Partners Rely on Datto EDR
Endpoint detection and response (EDR) is crucial for business security. Take a look at the seven biggest reasons why IT professionals and businesses rely on Datto EDR and learn more about how it can benefit you. Learn why features like continuous monitoring and automated threat response combined with ransomware rollback make Datto EDR the clear winning choice for endpoint security.
Did you miss…Vonahi’s Top 10 Critical Pentest Findings for 2024 report? DOWNLOAD IT>>


Explore the nuts and bolts of ransomware and see how a business falls victim to an attack. GET EBOOK>>




The top 3 vPenTest findings are eye-opening
One of the most effective ways for information technology (IT) professionals to uncover a company’s weaknesses before the bad guys do is penetration testing. By simulating real-world cyber attacks, penetration tests, sometimes called pentests, provide invaluable insights into an organization’s security posture, revealing weaknesses that could potentially lead to data breaches or other security incidents. Vonahi Security, the creators of the revolutionary vPenTest automated penetration testing platform, recently released the 2024 version of their annual Top 10 Critical Pentest Findings report, detailing the vulnerabilities they uncovered through more than 10,000 automated network pentests in 2023. Here are the top three findings and recommendations for preventing exploitation.
Excerpted in part from Vonahi Security’s Top 10 Critical Pentest Findings
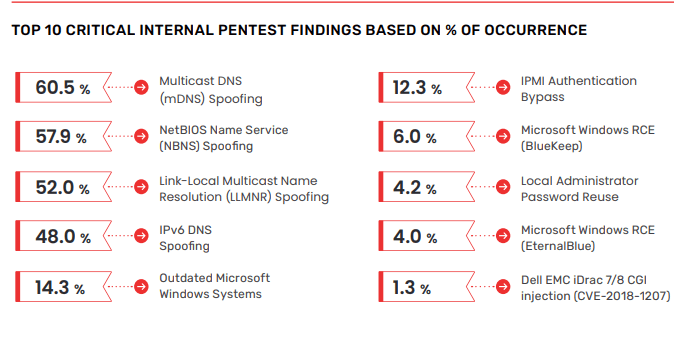

Source: Vonahi Security


See why choosing a smarter SOC is a smart business decision. DOWNLOAD AN EBOOK>>
01 (MDNS) SPOOFING SECURITY IMPACT
Multicast DNS (mDNS) is a protocol used within small networks to resolve a domain name system (DNS) name when a local DNS server does not exist.
When a system attempts to resolve a DNS name, the system proceeds with the following steps:
- The system checks its local host file to determine if an entry exists to match the DNS name in question with an IP address.
- On small networks where no DNS Server is configured, the system then uses mDNS to send an IP multicast query message to the systems on the local subnet that asks the host having that name to identify itself. Attackers can take advantage of this by answering this request and impersonating a system on the network.
Recommendations
The most effective method for preventing exploitation is to disable mDNS altogether if it is not being used. Depending on the implementation, this can be achieved by disabling the Apple Bonjour or Avahi-daemon service.
Reproduction steps
On a system configured with mDNS, attempt to interact with a DNS name that is known to be invalid (e.g. test123.local). On another system, use a network packet analyzer, such as Wireshark, to inspect the mDNS traffic on the internal network environment by filtering for UDP queries over port 5353.
Security impact
Rating CVSS3.1: 9.8
Since the mDNS queries are sent to systems on the local subnet, any system can respond to these queries with the IP address of the DNS name in question. This can be abused by malicious attackers since an attacker can respond to all of these queries with the IP address of the attacker’s system. Depending on the service that the victim was attempting to communicate with (e.g. SMB, MSSQL, HTTP, etc.), an attacker may be able to capture sensitive cleartext and/or hashed account credentials. Hashed credentials can, many times, be recovered in a matter of time using computing modern-day computing power and brute force techniques.


See how security awareness training stops the biggest security threats! GET INFOGRAPHIC>>
2. NETBIOS NAME SERVICE (NBNS) SPOOFING
NetBIOS Name Service (NBNS) is a protocol used amongst workstations within an internal network environment to resolve a domain name system (DNS) name when a DNS server doesn’t exist or can’t be helpful.
When a system attempts to resolve a DNS name, the system proceeds with the following steps:
- The system checks its local host file to determine if an entry exists to match the DNS name in question with an IP address.
- If the system does not have an entry in its local hosts file, the system then sends a DNS query to its configured DNS server(s) to attempt retrieving an IP address that matches the DNS name in question.
- If the configured DNS server(s) cannot resolve the DNS name to an IP address, the system then sends an NBNS broadcast packet on the local network to seek assistance from other systems.
Recommendations
The following are some strategies for preventing the use of NBNS in a Windows environment or reducing the impact of NBNS Spoofing attacks:
- Configure the UseDnsOnlyForNameResolutions registry key in order to prevent systems from using NBNS queries (NetBIOS over TCP/IP Configuration Parameters). Set the registry DWORD to 1.
- Disable the NetBIOS service for all Windows hosts in the internal network. This can be done via DHCP options, network adapter settings or a registry key.
Reproduction steps
On a system configured with NBNS, attempt to interact with a DNS name that is known to be invalid (e.g. test123.local). On another system, use a network packet analyzer, such as Wireshark, to inspect the broadcasted traffic on the internal network environment.
Security impact
Rating: VSS3.1: 9.8
Since the NBNS queries are broadcast across the network, any system can respond to these queries with the IP address of the DNS name in question. This can be abused by malicious attackers since an attacker can respond to all of these queries with the IP address of the attacker’s system. Depending on the service that the victim was attempting to communicate with (e.g. SMB, MSSQL, HTTP, etc.), an attacker may be able to capture sensitive cleartext and/ or hashed account credentials. Hashed credentials can, many times, be recovered in a matter of time using modern-day computing power and brute force techniques.


Learn to defend against today’s sophisticated email-based cyberattacks DOWNLOAD EBOOK>>
3. LINK-LOCAL MULTICAST NAME RESOLUTION (LLMNR) SPOOFING
Link-Local Multicast Name Resolution (LLMNR) is a protocol used amongst workstations within an internal network environment to resolve a domain name system (DNS) name when a DNS server does not exist or cannot be helpful.
When a system attempts to resolve a DNS name, the system proceeds with the following steps:
- The system checks its local host file to determine if an entry exists to match the DNS name in question with an IP address.
- If the system does not have an entry in its local hosts file, the system then sends a DNS query to its configured DNS server(s) to attempt retrieving an IP address that matches the DNS name in question.
- If the configured DNS server(s) cannot resolve the DNS name to an IP address, the system then sends an LLMNR broadcast packet on the local network to seek assistance from other systems.
Recommendations
The most effective method for preventing exploitation is to configure the Multicast Name Resolution registry key in order to prevent systems from using LLMNR queries.
- Using Group Policy: Computer Configuration\Administrative Templates\Network\DNS Client \Turn off Multicast Name Resolution = Enabled (To administer a Windows 2003 DC, use the Remote Server Administration Tools for Windows 7)
- Using the Registry for Windows Vista/7/10 Home Edition only: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\ Windows NT\DNSClient \EnableMulticast
Reproduction steps
On a system configured with LLMNR, attempt to interact with a DNS name that is known to be invalid (e.g. test123.local). On another system, use a network packet analyzer, such as Wireshark, to inspect the broadcasted traffic on the internal network environment.
Security impact
CVSS3.1: 9.8
Since the LLMNR queries are broadcast across the network, any system can respond to these queries with the IP address of the DNS name in question. This can be abused by malicious attackers since an attacker can respond to all of these queries with the IP address of the attacker’s system. Depending on the service that the victim was attempting to communicate with (e.g. SMB, MSSQL, HTTP, etc.), an attacker may be able to capture sensitive cleartext and/or hashed account credentials. Hashed credentials can, many times, be recovered in a matter of time using modern-day computing power and brute-force techniques.
Elevate Your Security with vPenTest: The Ultimate Automated Network Penetration Testing Solution
vPenTest is the premier, fully automated network penetration testing platform designed to proactively minimize security risks and breaches across your organization’s IT environment. By eliminating the need to source qualified network penetration testers, vPenTest delivers high-quality results that clearly outline identified vulnerabilities, assess their risks, and provide strategic and technical remediation guidance. Additionally, it enhances your compliance management capabilities effortlessly. The benefits of vPenTest are unbeatable
- Comprehensive assessments made easy: With vPenTest, conduct both internal and external network penetration tests seamlessly, ensuring every potential entry point in your network infrastructure is meticulously examined.
- Real-world simulation: Experience real-world cyber threat simulations with vPenTest, gaining invaluable insights into your security posture and preparedness against malicious actors.
- Timely and actionable reporting: Post-testing, vPenTest provides detailed, yet easy-to-understand reports, highlighting vulnerabilities, their potential impacts, and recommended mitigation actions, ensuring you’re always a step ahead.
- Ongoing penetration testing: Stay proactive with vPenTest’s affordable monthly testing intervals, maintaining a robust security posture that swiftly adapts to emerging threats.
- Efficient incident response: By identifying vulnerabilities proactively, vPenTest ensures you’re better prepared to respond to potential security incidents efficiently and effectively.
- Compliance alignment: vPenTest aligns seamlessly with regulatory compliance requirements such as SOC2, PCI DSS, HIPAA, ISO 27001, and cyber insurance mandates, simplifying your compliance management process.
Transform your security approach with vPenTest—your trusted partner in automated network penetration testing. Ensure comprehensive, real-time protection and compliance, all while streamlining your security operations. BOOK A DEMO NOW>>


The Top Cyberattack Trends of 2024
June 19, 2024 I 1 PM ET / 10 AM PT
In 2023, cyberattacks surged by 35%, costing businesses over $4.2 billion. As threats continue to evolve, understanding these trends is imperative. In this informative session, host Miles Walker will guide you through the top cyberthreats businesses face right now. You’ll learn:
- The most dangerous of emerging cyberthreats.
- Effective cybersecurity strategies.
- Lessons from recent high-profile attacks.
Save your spot and stay up-to-date on the top cyberattack trends! REGISTER NOW>>
June 19: The Top Cyberattack Trends of 2024 REGISTER NOW>>
June 18: Kaseya+Datto Connect Local Toronto (Security and Compliance Series) REGISTER NOW>>
October 28 – 30: Kaseya DattoCon (Miami) REGISTER NOW>>
November 12 – 14: Kaseya DattoCon APAC (Sydney) REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!