The Week in Breach News: 10/19/22 – 10/25/22

Cyberattacks sour the year for wine merchants iDealwine and Vinomofo, Microsoft makes a configuration blunder and 6 reasons why prioritizing cybersecurity is vital for SMBs that may sway even the most skeptical decision-makers.

Give your clients the Cybersecurity Monster Hunter’s Checklist as a fun, Halloween-themed way to help them hunt down cybersecurity weaknesses. GET CHECKLIST>>

Microsoft
https://thehackernews.com/2022/10/microsoft-confirms-server.html
Exploit: Misconfiguration
Microsoft: Software Company

Risk to Business: 1.802 = Severe
Microsoft confirmed that it inadvertently exposed information related to thousands of customers following a misconfiguration of Azure Blob Storage. The company said in a statement that the misconfiguration “resulted in the potential for unauthenticated access to some business transaction data corresponding to interactions between Microsoft and prospective customers, such as the planning or potential implementation and provisioning of Microsoft services”. The misconfiguration of the Azure Blob Storage was spotted on September 24, 2022. Microsoft states that the exposed data included names, email addresses, email content, company name, and phone numbers and attached files relating to business “between a customer and Microsoft or an authorized Microsoft partner.”
How It Could Affect Your Customers’ Business: Even the biggest companies can fall victim to human error and be stuck dealing with unpleasant consequences.
ID Agent to the Rescue: Get tips for identifying and stopping malicious insiders and mitigate accidental insider risks like human error in the Guide to Reducing Insider Risk. DOWNLOAD IT>>
MedStar Mobile Healthcare
https://www.cbsnews.com/dfw/news/medstar-reports-its-computer-network-was-hit-by-a-cyberattack/
Exploit: Ransomware
Medstar Mobile Healthcare: Ambulance Service



Risk to Business: 1.423 = Extreme
Emergency medical services and ambulance company MedStar in Texas was hit by a cyberattack that impacted its ability to dispatch ambulances and respond to 911 calls. The attack occurred on October 20. The company said that they quickly isolated connected systems to assure the breach was quarantined. MedStar was forced to resort to manually dispatching calls over a public safety radio until they could determine that computer systems were secure. The company said it does not think that PHI like 911 call records was accessed by the attackers.
How It Could Affect Your Customers’ Business: Ransomware is especially nasty in the healthcare sector because it leads to adverse patient outcomes.
ID Agent to the Rescue: See the biggest risks that different sectors face today and get a look at what your clients will be facing tomorrow in The Global Year in Breach 2022. DOWNLOAD IT>>


Just getting started in cybersecurity? This resource bundle will help you get up to speed to protect your clients fast! GET IT>>


United Kingdom – Kingfisher Insurance
https://techmonitor.ai/technology/kingfisher-insurance-ransomware-lockbit
Exploit: Ransomware
Kingfisher Insurance: Insurer






Risk to Business: 2.107 = Severe
Kingfisher Insurance has been hit by a ransomware attack courtesy of LockBit 3.0. The cybercrime group claims to have lifted 1.4 terabytes of information from the company. That data may include the personal data of employees and customers. The gang has demanded that Kingfisher pay the unspecified ransom by November 28 to avoid having the data published. The gang released a sample of the stolen data as proof including information from management system accounts and passwords from Workaday and Access databases.
How It Could Affect Your Customers’ Business: Ransomware practitioners are especially interested in service and supply chain businesses because of all of the information they store.
ID Agent to the Rescue: Go over the Cybersecurity Risk Protection Checklist with your clients to make sure that they’re covering all of their security bases. GET CHECKLIST>>
Germany – Metro Cash and Carry
Exploit: Hacking
Metro Cash and Carry: Hospitality Wholesaler



Risk to Business: 1.624 = Severe
Hospitality wholesale giant Metro is experiencing infrastructure outages and store payment issues following a cyberattack. The IT outages have been affecting stores in Austria, Germany and France since at least October 17, although the company’s stores remain in operation. Metro says that it was forced to set up offline payment systems and that customers should expect online orders to be delayed. No word on if any data was exposed or stolen was available at press time.
How it Could Affect Your Customers’ Business: Supply chain cyberattacks have been an increasing burden for wholesalers in every sector.
ID Agent to the Rescue: Are you confident that you’re providing the right security training for your clients? The Security Awareness Training Guide for MSPs helps you make sure. DOWNLOAD IT>>
France – iDealwine
https://www.helpnetsecurity.com/2022/10/19/idealwine-data-breach/
Exploit: Hacking
iDealwine: Online Wine Marketplace





Risk to Business: 2.619 = Moderate
eMerchant iDealwine was knocked offline by hackers for several days. iDealwine has disclosed that it experienced a data breach as a result of the incident. The French company specializes in online auctions and fixed-price sales of fine wine and also offers customers information about news and trends in the wine industry. The company’s website has since been restored.





Individual Risk: 2.702 = Moderate
It has informed its customers that their name, address, telephone number and email address may have been compromised. The company was quick to note that customers’ credit card/bank information has not been compromised.
How it Could Affect Your Customers’ Business: Retail businesses have been experiencing a high level of cybersecurity trouble in 2022.
ID Agent to the Rescue: Curious to see if you’re offering your clients the right dark web monitoring solution? Explore your options with The Dark Web Monitoring Buyer’s Guide for MSPs. DOWNLOAD IT>>



Give your clients this infographic to start a conversation about getting on the path to zero trust. GET INFOGRAPHIC>>


Singapore – Carousell
Exploit: Hacking
Carousell: Online Retail Marketplace






Risk to Business: 1.684 = Severe
A database of user accounts believed to have been stolen from online marketplace Carousell is being sold on the dark web. Carousell said on Friday that 1.95 million user accounts were compromised after a bug was introduced during a system migration, giving bad actors a quick path inside the company’s systems. It assured users that no credit card and payment-related information was compromised. Hackers uploaded the 2GB database on Oct 12, two days before Carousell confirmed the breach. In an interesting twist, the hackers said they will be selling only five copies of the database.
How it Could Affect Your Customers’ Business: Retailers need to be especially careful about security as we head into the winter holiday season.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>


Spark profitable security training conversations with clients & prospects by giving them this list of risks. DOWNLOAD IT>>


Australia – EnergyAustralia
Exploit: Hacking
EnergyAustralia: Electricity Utility





Risk to Business: 2.783 = Moderate
EnergyAustralia has become the latest company to be targeted by a cyber-attack, with hundreds of customers’ details exposed. In a statement released late on Friday, the electricity company said 323 residential and small business customers were affected by unauthorized access to their online platform, My Account. The company said there was “no evidence” customer details were transferred outside the company’s platform. They also said sensitive documents such as driver’s licenses or passports were not stored on the platform. No other EnergyAustralia systems were affected. The breach occurred in late September and customers were informed in October.





Individual Risk: 2.801= Moderate
Details including customer names, addresses, email addresses, electricity and gas bills, phone numbers and the first six and last three digits of their credit cards are all included with those accounts.
How it Could Affect Your Customers’ Business: Utility companies in Australia have had a rough fall as cybercriminals continue to hammer Australian organizations.
ID Agent to the Rescue: Sell clients on the benefits of security and compliance training with the bottom-line data in The Business Case for Security Awareness Training. DOWNLOAD IT>>
Australia – Vinomofo
https://itwire.com/business-it-news/security/vinomofo-suffers-security-breach.html
Exploit: Hacking
Vinomofo: Online Wine Marketplace






Risk to Business: 1.771 = Severe
Online wine sales company Vinomofo has disclosed a data breach after an intruder accessed customers’ personal information. Hackers gained access to Vinomofo’s client records through a test platform that the company was using as part of a new website rollout. Vinomofo discovered signs of the breach on September 27. In a statement, the company said that it doesn’t hold identity or financial data such as passports, driver’s licenses or credit cards/bank details. The company did not say how many of its customers were impacted in this breach.






Individual Risk: 1.837 = Severe
Names, addresses, emails, gender identities, phone numbers and dates of birth may have been accessed by bad actors in this incident.
How it Could Affect Your Customers’ Business: Unfortunately, online retailers have been experiencing a high level of cyberattacks in 2022.
ID Agent to the Rescue: A comprehensive security awareness training program is critical for reducing cyber risk and keeping companies safe from trouble. DOWNLOAD IT>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


See how today’s biggest threats may impact your MSP and your customers in our security blogs.
- Wiper Malware: The Nastiest Cyberthreat in Town
- What Tools and Techniques Are Used in BEC Attacks?
- 3 Growing Dark Web Dangers Businesses Face Right Now
- Why You Should Be Worried About This Devastating (& Growing) Cyber Threat
- The Week in Breach News: 10/12/22 – 10/18/22


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>


Newly Refreshed: the Data Security & Privacy Compliance Campaign
The latest iteration of this popular campaign will help you grow your business and show your clients great ways to protect their data.
How does this campaign help MSPs?
This campaign gives MSPs tools to help organizations understand the importance — and challenges — of maintaining data security and privacy compliance protocols, particularly if their employees operate in a hybrid work environment. Show companies how they can protect their sensitive data and what to do in the event of a breach. This campaign maps well to services you can offer like Compliance Manager GRC and RocketCyber.
Why your clients will respond to it:
Data is critical to your clients’ companies, and it’s increasingly become the target of cybercriminals looking to profit from its theft. If a breach includes legally protected data such as Personally Identifying Information (PII), the ensuing penalties can compound the loss. This campaign helps clients discover how their organization can proactively implement measures to detect and prevent cyber threats before they result in a costly incident.
LEARN MORE & SEE THE CAMPAIGN>>
Do you need some extra help making the most of these campaigns? Check out our Quick Start Guide for help learning how to use the Pro Campaigns.
Not signed up for Powered Services Pro? You’re missing out on an arsenal of sales and marketing tools to help you make more money. What are you waiting for? SIGN UP NOW>>



Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>


Can You Survive a Cybersecurity Horror Story? These Tools Can Help You Make It Through!
Monsters of Cybersecurity – In this eBook, take a look at the horrors of cybercrime plus spine-chilling cyberattacks and how to prevent them! GET EBOOK>>
The Cybersecurity Monster Hunter’s Checklist – Make sure you’re defeating all of the monsters of cybersecurity with this checklist. GET CHECKLIST>>
Cyberattacks: The Good, The Bad and Downright Ugly -Join Miles Walker for tales of cybersecurity adventure as you explore some of today’s weirdest cyberattacks. LISTEN NOW>>
Did you miss…? The Complete IAM Checklist DOWNLOAD IT>>



See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>




6 Reasons Why SMBs Businesses Neet to Prioritize Cybersecurity Investment
These data points should sway even the most hardened skeptics!
Cybersecurity needs to be a top priority for businesses of every size. But it may be challenging to get that message through to small business owners looking for ways to economize. The fact is, 60% of businesses shutter within 6 months of a successful cyberattack. Explaining some of the concrete reasons why a cybersecurity incident could be a disaster for even a very small business may help illuminate the danger of neglecting cybersecurity to business owners who are skeptical of spending money on something that they don’t think they need or won’t provide immediate, obvious value to their business.



Learn how a new integration between BullPhish ID & Graphus saves time & money. SEE THE DETAILS>>
Big businesses take cybersecurity seriously, but too many small businesses don’t
C-suite executives in major corporations and large businesses take cybersecurity seriously. They’re cognizant of just how damaging an incident could be for their company. In a recent survey by Price Waterhouse Cooper, cybersecurity was designated as the top risk businesses faced. An estimated 40% of all respondents listed the increasing frequency and seriousness of cyber attacks as a serious risk with a further 38% calling it a moderate risk. Diving deeper, executives in all high-end roles ranked cyber attacks high on their list of concerns, including board members (51%), tax leaders (47%), CFOs (44%) and CMOs (41%). That pattern is expected to continue – Gartner speculates that by 2026, 50% of C-level executives will have cybersecurity performance requirements written into their employment contracts.
However, that attitude doesn’t necessarily carry into smaller businesses. A CNBC /Momentive Small Business Survey details the attitudes toward cybersecurity that they measured from SMB owners and managers. The biggest takeaway: SMB execs aren’t on the same page as their counterparts in larger organizations. Unfortunately, 56% of the SMB owners surveyed said they are “not very concerned” about being the victim of a cyberattack in the next 12 months, and among those, 24% said they were “not concerned at all.” The researchers determined that SMB owners were generally quite confident (59%) that even if they were hit with a cyberattack, they’d quickly resolve it. Only 37% were “not very confident” and only 11% were “not confident at all.”



See five things that you can do to reduce nation-state cyber threat risk for your clients fast. GET CHECKLIST>>
6 Reasons Why SMBs Need to be Worried About Cybersecurity
You know how critical cybersecurity is to a company’s continued success, but you may need additional data to clarify that for some decision-makers. These six reasons why it’s important to invest in cybersecurity to avoid business disasters may help get the message across.
1. Cyberattacks are more expensive than SMB owners think
A survey by insurance giant Nationwide showed that 40% of small business owners surveyed expect a cyberattack to cost less than $1,000 and another 60% think it would take less than three months to fully recover. That is definitely not the case. Instead, an analysis of Nationwide’s claims data revealed that cyber claims range between $15,000 to $25,000 in recovery costs. That doesn’t include costs associated with the restoration process, reputational damage, any ransom paid or regulatory/legal trouble. Nationwide’s researchers also determined that the average recovery time for a business after a general successful cyberattack attack is 279 days.
2. Lost productivity hurts
One successful cyberattack like a ransomware event could take a huge bite out of a company’s productivity. For example, experts estimate that 25% of businesses that fall victim to a ransomware attack are forced to close temporarily due to the inability to operate thanks to a loss of access to IT systems and data. Many companies can’t weather a closure or loss of operational capacity, even for a few days, especially if the organization in question is in a time-sensitive field like healthcare or critical infrastructure. Downtime can be extensive too, and that’s also getting worse depending on the nature of the incident as attacks grow more sophisticated. IBM researchers determined that a data breach caused by a ransomware attack took the businesses that they studied 237 days to identify and 89 days to contain, for a total lifecycle of 326 days. Compared to the overall average lifecycle of 277 days, organizations took 49 days longer to identify and contain a ransomware attack, a difference of 16.3%.
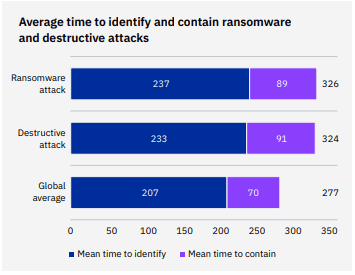

Source: IBM


Help your clients make sure they’ve got their identity & access management bases covered. GET CHECKLIST>>
3. Cyberattack damage lingers for years
But a cyberattack isn’t usually a straightforward, one-and-done emergency with a fixed cost. The damage sticks around, causing problems for months or even years. After paying for immediate investigation, mitigation and repair, the bills from a cyberattack don’t stop coming. In industries that are not heavily regulated, a little over three-quarters of the cost of a data breach is paid in the first year after the incident. In highly regulated fields, only 44% of the cost of a data breach is paid in the first year. Around 61% of the cost of a data breach is paid in the first year after impact, an estimated 24% comes due in the next 12 to 24 months, and the bills for the final 15% can arrive more than two years later.
4. Reputation damage is real and serious
Reputation matters in business and a successful cyberattack can spell doom for a company’s good name with both other businesses and consumers. In the aftermath of something like a ransomware attack or business email compromise scheme, the victim company’s brand suffers. A report by IBM and Forbes Insights found that 46% of organizations that experienced a cybersecurity breach suffered a major hit to their reputation, reducing their brand’s value as a result. The ensuing reputational damage can negatively impact a company’s business relationships. Over 60% of respondents to a Ponemon Institute report on third-party security practices said that they rely on a company’s reputation for responsible cybersecurity practices when considering a business relationship.



Give your clients this infographic to start a conversation about getting on the path to zero trust. GET INFOGRAPHIC>>
5. The whole IT environment is damaged in a cyberattack
A cyberattack like a ransomware infection doesn’t just impact a small section of a company’s IT environment. It bleeds out into many areas, snarling productivity and recovery at the same time. Which environments in an organization does ransomware impact? Storage systems and cloud-based data storage tops the list, hit in more than Storage systems or cloud-based data account for 79% of impacted environments in successful ransomware attacks, but other key elements that impact an organization’s ability to do business also take a hit when that organization is struck down by a ransomware attack.
Environments Impacted by a Ransomware Attack
| Storage systems | 40% |
| Cloud-based data | 39% |
| Networks/connectivity | 37% |
| Key IT infrastructure | 36% |
| Data protection infrastructure | 36% |
Source: Hitachi


Go inside BEC scams & get tips to keep businesses safe from today’s most expensive cyberattack. DOWNLOAD EBOOK>>
The problem is serious now and will only get worse in the future.
It’s unlikely that most SMBs are ready to face the specter of a damaging cyberattack. IBM discovered that 60% of business leaders admitted that their company didn’t have a cyberattack prevention plan at all. They’re definitely not ready to face the expense of the whole thing. An estimated 83% of small businesses haven’t put cash aside for dealing with a cyberattack. Even more alarming, one-quarter of SMB owners told researchers in an insurance industry survey said that they didn’t even know that cyberattacks would cost their companies money.
Cybercrime isn’t going to stop growing whether businesses are ready to handle the possibilities or not. Cybersecurity Ventures anticipates that global cybercrime costs will rise by 15% yearly over the next five years up to $10.5 trillion annually by 2025. That estimate takes into account a wide variety of factors including damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data and systems, and reputational harm.
We Can Help You Mitigate Your Clients’ Risk of a Cybersecurity Nightmare
Our suite of powerful security solutions can help you keep your clients safe from today’s nastiest cyberattacks at a price you’ll both love.
Security awareness and compliance training plus phishing simulation
BullPhish ID is the ideal security and compliance awareness training solution for companies of any size. This powerhouse is the channel leader in phishing simulations.
- An extensive library of security and compliance training videos in eight languages
- Plug-and-play or customizable phishing training campaign kits
- New videos arrive 4x per month and new phishing kits are added regularly
- Easy, automated training delivery through a personalized user portal
You’ll love our latest integration between BullPhish ID and Graphus! If you’re already using BullPhish ID for security and compliance awareness training and phishing simulations, you’ll love our latest integration Advanced Phishing Simulations (Drop-A-Phish). This feature leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users when running phishing simulations. LEARN MORE>>
Dark web monitoring
Dark Web ID offers best-in-class dark web intelligence, reducing credential compromise risk.
- 24/7/365 monitoring using real-time, machine and analyst-validated data
- Fast alerts of compromises of business and personal credentials, including domains, IP addresses and email addresses
- Live dark web searches find compromised credentials in seconds
- Create clear and visually engaging risk reports
Identity and Access Management (IAM)
Passly is the perfect multi-tool for IAM packing four essentials into one affordable package
- Get two-factor authentication (2FA), single sign-on, secure password vaults with one solution
- Simple, intuitive remote management
- Roll it out in a snap with easy deployment and seamless integration with common business applications
Automated, AI-powered antiphishing email security
Graphus AI-enabled, automated email security that catches 99.9% of sophisticated phishing threats and offers amazing benefits.
- Forget old-fashioned safe sender lists. Graphus analyzes the content of messages using more than 50 points of comparison to suss out fakes fast.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- 3 layers of powerful protection at half the cost of competing solutions
- Don’t waste time on fussy configurations or adding threat reports. AI does that for you, getting everything up and running with just a few clicks and minimal maintenance.


Make sure your clients have all the bases covered with the Computer Security To-Do Checklist! GET IT>>


EVENT TODAY!!! Do You Have What it Takes to be a Cybersecurity Jeopardy Champion?
It’s time to match wits with other IT professionals and our special guests on October 26 at 2 pm ET to see who will be crowned our Cybersecurity Jeopardy champion! Plus, every attendee has the opportunity to win one of the many fun prizes we’ll be awarding throughout the event! Reserve your seat today! REGISTER NOW>>
October 25-26: Southwest US Summit REGISTER NOW>>
November 2-3: ChannelPro SMB Forum 2022: Los Angeles REGISTER NOW>>
December 6: Connect IT Local – Atlanta REGISTER NOW>>
December 8: Connect IT Local – Miami REGISTER NOW>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this content. When you get a chance, email [email protected] to let us know how our content works for you!