The Week in Breach News: 05/18/22 – 05/24/22

Multiple attacks disrupt education and expose data at U.S. public schools, a novel response to a ransom demand in Zambia and insight into the influences that are driving risk in The State of Email Security 2022.

Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>


Chicago Public Schools
https://www.securityweek.com/breach-exposed-data-half-million-chicago-students-staff
Exploit: Supply Chain Risk
Chicago Public Schools: Regional Education Agency








Risk to Business: 1.944 = Severe
Chicago Public Schools is facing a big breach of student data after a technology vendor experienced a data security incident. CPS has disclosed that it was recently informed that an unauthorized access incident took place at Battelle for Kids in December 2021. In that incident, a server that housed four years’ worth of personal information about students and staff from the 2015-16 through 2018-2019 school years was breached. Officials say that no Social Security numbers, no financial information, no health data, no current course or schedule information, no home addresses and no course grades, standardized test scores, or teacher evaluation scores were exposed in this incident.








Risk to Individual: 1.672 = Severe
The improperly accessed data included students’ names, schools, dates of birth, gender, CPS identification numbers, state student identification numbers, class schedule information and scores on course-specific assessments used for teacher evaluations. Employee data included names, employee identification numbers, school and course information and emails and usernames.
How It Could Affect Your Customers’ Business: School system databases are popular targets because they often hold big stores of information.
ID Agent to the Rescue: A strong security culture reduces the risk of an incident. Help your clients build one with The Building a Strong Security Culture Checklist! DOWNLOAD IT>>
Fort Sumner Municipal Schools (New Mexico) & Washington Local Schools (Ohio)
https://therecord.media/k-12-cyberattacks-new-mexico-ohio/
Exploit: Ransomware
Fort Sumner Municipal Schools (New Mexico) & Washington Local Schools (Ohio): Local Education Agency








Risk to Business: 1.804 = Severe
The Cl0p ransomware gang has posted information that points to a successful ransomware attack against the Fort Sumner Municipal Schools agency in New Mexico. The Superintendent of Schools in the district confirmed the incident. This is just the latest in a long string of ransomware attacks that have impacted public school systems in the US. Just this week, the Washington Local Schools district in Ohio was also hit with a ransomware attack, this time impacting the district’s phone, email, internet and WiFi networks as well as Google Classroom.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business Bad actors know that using ransomware against targets with time-sensitive business can be profitable.
ID Agent to the Rescue: Learn to mitigate your clients’ ransomware risk and protect them from trouble with the resources in our Deep Dive Into Ransomware bundle! GET BUNDLE>>
The U.S. Drug Enforcement Agency (DEA)
Exploit: Hacking
The U.S. Drug Enforcement Agency (DEA): Federal Government Agency








Risk to Business: 1.763 = Severe
Officials are investigating a potential breach that could allow bad actors to access key systems used by law enforcement agencies in the U.S. A tip pointed officials to information that the LAPSUS$ hacking group may have gained access to the esp.usdoj.gov data portal, the Law Enforcement Inquiry and Alerts (LEIA) system, the U.S. Drug Enforcement Agency (DEA)’s El Paso Intelligence Center (EPIC) and other DEA systems. That unauthorized access may be used by cybercriminals in myriad ways including for impersonation efforts and doxing, as well as affording the bad guys the opportunity to search databases and to obtain sensitive data.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How It Could Affect Your Customers’ Business: This kind of access and information in the wrong hands could be beneficial to cybercriminals including nation-state actors.
ID Agent to the Rescue: Find and slay dastardly vulnerabilities in your clients’ security strategy and emerge victorious with The Cybersecurity Monster Hunter’s Checklist! GET IT>>


Find the right dark web monitoring solution for your customers & your MSP with this checklist! DOWNLOAD IT>>


Greenland – Agency for Health and Prevention
https://therecord.media/greenland-cyberattack-healthcare-systems/
Exploit: Hacking
Agency for Health and Prevention: National Agency


Risk to Business: 2.864 = Moderate
The government of Greenland has announced that healthcare services have become extremely limited as a result of a cyberattack. While the nature of the incident was not specified, government officials noted that the network for the entire system had to be shut down, resulting in medical care providers becoming unable to access patient records and creating delays in care. The government says that patient data is not at risk, and that emergency treatment will not be impacted.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business: Healthcare targets have been at the top of the cybercriminal hit list since the start of the pandemic.
ID Agent to the Rescue: Help your clients be ready for cybercrime trouble and keep their data safe with The Computer Security To-Do List. DOWNLOAD IT>>


Learn how to spot and stop malicious insiders and educate users with this handy infographic! GET IT>>


Zambia – National Bank of Zambia
Exploit: Ransomware
National Bank of Zambia: Banking & Financial Services








Risk to Business: 1.917 = Severe
A cyberattack at the National Bank of Zambia has played out with a bizarre twist. After experiencing a ransomware attack by the Hive ransomware outfit that purportedly encrypted the bank’s Network Attached Storage (NAS) device, officials responded to the cybercriminals’ ransom demands with a refusal to pay. Bloomberg reports that the refusal was accompanied by images of male genitalia and a message referencing a common NSFW insult about what the bad guys could do with their demands. In a statement, the bank said that it had experienced an incident that impacted some systems such as the Bureau De Change Monitoring System and the bank’s website.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business Organizations in the Banking & Finance sector suffered the most cyberattacks in 2021, and pressure isn’t letting up.
ID Agent to the Rescue Go behind the scenes to learn more about ransomware and how to defend against it (plus who profits from it) in our eBook Ransomware Exposed. GET EBOOK>>
South Africa – Dis-Chem
https://www.infosecurity-magazine.com/news/pharmacy-giant-data-breach/
Exploit: Supply Chain Risk
Dis-Chem: Pharmaceutical Company








Risk to Business: 1.733-Severe
Major pharmaceutical retailer Dis-Chem recently announced that it had been hit by a data breach that may have exposed the personal details of 3.6 million customers thanks to a data security incident at a third-party service provider on May 1, 2022. Dis Chem is the second-largest retail pharmacy chain in South Africa. An investigation is underway, and the company has stated that it will not be offering further comment on the incident.








Risk to Business: 1.733-Severe
The investigation has determined that the incident affected a total of 3,687,881 data subjects so far, exposing subjects’ first name and surname, email addresses, and cell phone numbers.
How it Could Affect Your Customers’ Business Defense industry contractors and military-adjacent service providers are tempting targets for cybercriminals looking for back doors.
ID Agent to the Rescue Get an in-depth look at how ransomware is evolving and who profits from it in our hit eBook Ransomware Exposed. GET THIS EBOOK>>



Learn to unleash the power of checklists and other downloads in your marketing efforts! WATCH WEBINAR>>


Singapore – Nikkei Business Publications
Exploit: Ransomware
Nikkei Business Publications: Publishing Company


Risk to Business: 2.786 = Moderate
Asian publishing giant Nikkei has disclosed that the organization’s headquarters was hit by a ransomware attack on May 13, 2022. The company, the publisher of several business and technology magazines, said that it is still investigating the incident and has not yet determined if bad actors accessed customer data. Officials in both Singapore and Japan have been notified.
Individual Impact: No information about consumer/employee PII, PHI or financial data exposure was available at press time.
How it Could Affect Your Customers’ Business More than half of APAC organizations experienced a cyberattack in 2021.
ID Agent to the Rescue Help your clients increase their cyber resilience with the tips in The Road to Cyber Resilience eBook and you can give them an edge against cyberattacks. GET IT>>


Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>


1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
Risk scores for The Week in Breach are calculated using a formula that considers a range of factors for each incident


Go Inside the Ink to see how today’s biggest threats can impact your MSP and your customers in our blog.
- Developing an Effective Security & Compliance Awareness Program
- Today’s Booming Dark Web Economy Heightens Ransomware Risk
- 7 Factors That Influence Phishing Risk
- The Secret to Building a Great Security & Compliance Awareness Training Program
- The Week in Breach News: 05/11/22 – 05/17/22


Just getting started in cybersecurity? This resource bundle will help you get up to speed to protect your clients fast! GET IT>>


Fresh Resources
Gain Insight Into Digital Risk Protection from the MSP Security Roundtable Series & More
MSP Cybersecurity Roundtable: How Infrastructure Attacks Can Hurt Every Business – WATCH NOW>>
MSP Cybersecurity Roundtable: Nation-State Hacking is Everyone’s Problem Now – WATCH NOW>>
Make sure you’re covering all the bases with the Are Your Users Trained to Handle These Risks? checklist. DOWNLOAD IT>>
Did you miss… The handy infographic Can You Spot a Phishing Email? – it’s perfect for social media! DOWNLOAD IT>>


Can you spot a phishing message? This infographic points out red flags to watch for to sniff them out! DOWNLOAD IT>>




The State of Email Security in 2022 is Perilous
See why your clients need strong email security now more than ever
The State of Email Security 2022 from Graphus has just been released, and it brings some important information to the table: the state of email security for businesses these days is dire. The risk of trouble that every business faces from phishing is high and rising. Businesses are constantly being barraged by phishing messages and the pace isn’t slowing down. 84% of businesses in a new study said that they were the victims of a successful phishing attack in 2021, a 15% increase over the same 12-month period in 2020.
Making defense even more challenging, the cybercriminal playbook is evolving, delivering new phishing attempts to employee inboxes every day. Bad actors have been continually improving their social engineering techniques, and finding success in sophisticated attacks, like masquerading as a trusted contact or impersonating well-known brands. The emergence of cybercrime-as-a-service, the explosive growth of ransomware and elevated nation-state cybercrime risk have also complicated the email security picture. This snapshot of the factors that influence today’s defensive challenges and variables that may help you ensure that your clients have the right protection in place to reduce their exposure to trouble.



Learn to unleash the power of checklists and other downloads in your marketing efforts! WATCH WEBINAR>>
Malicious Attachments and BEC Are Dominant Risks
AI technology and security automation have been powerful tools in the fight against phishing. Graphus’ proprietary technology, TrustGraph, thoroughly analyzes the content of every incoming email an organization protected with the solution receives. Phishing messages are detected and subsequently quarantined. In a breakdown of the threats detected in the email that TrustGraph analyzed in 2021, it’s clear that two major risks dominated, occupying big slices of the pie.
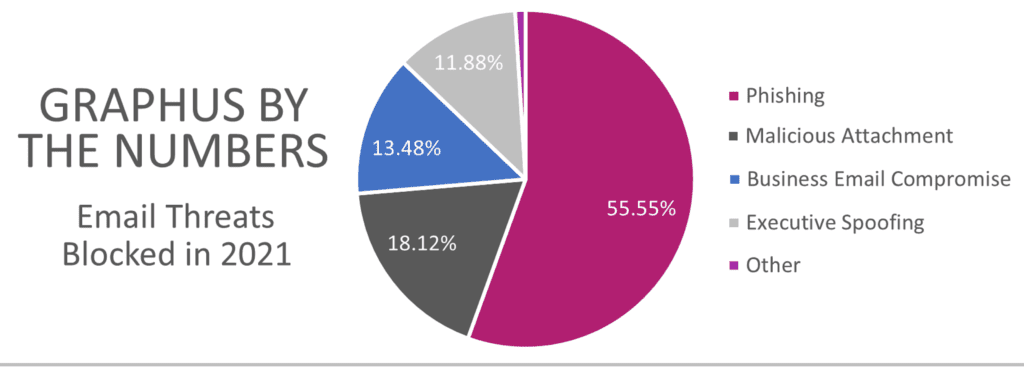

3 Trends Shaped Email Security Risk in 2021
There wasn’t a central cause that could be identified as the culprit behind soaring phishing risk in 2021, unlike in 2020 when the influence of the pandemic was obvious. Many factors added to the load of risk, making it harder for security teams to defend against because of the constantly shifting nature of the risk factors that they faced. However, these three phishing-related cybercrime trends were instrumental in shaping the current state of email security.
1. Ransomware vs. infrastructure
Ransomware has emerged as a growing threat to infrastructure targets as cybercriminals seek big, fast payouts from time-sensitive and critically important sectors. The U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) began tracking infrastructure-related ransomware attacks in the United States in June 2021. Analysts noted at least one ransomware attack hit organizations in 14 of 16 official categories of infrastructure. Organizations that fall victim to a ransomware attack lose an estimated average of six working days, and 37% of them experience downtime of one week or more — something no critical infrastructure component can afford.
One major driver here is the cybercriminal search for information about operational technology (OT) and how that has impacted the ransomware picture for infrastructure assets and for other organizations in the Energy and Manufacturing sectors. Bad actors are on the hunt for many reasons, but two prominent ones stand out: gaining information about OT through ransomware attacks that gives the bad guys an edge in future attacks and gathering data about OT that can be sold. That’s an especially worrying circumstance when it comes to nation-state cybercrime, and it will continue to be a contributing factor in infrastructure risk moving forward.
In a study on the dangers that cyber dangers like ransomware attacks could have for operational technology, Mandiant analysts discovered that one in seven attacks gave the bad guys access to sensitive information about OT. Out of 3,000 data leaks originating from ransomware attacks, the study identified at least 1,300 exposures from critical infrastructure and industrial production organizations that use OT. Researchers found all manner of useful OT information exposed in dark web data dumps. While some of that data is of the routine (yet still dangerous) username and password variety, other types of data found in dark web dumps and forums included IP addresses, remote services, asset tags, original equipment manufacturer (OEM) information, operator panels and network diagrams.



Set businesses on the zero trust path with the 6 Tips for Implementing Zero Trust Security infographic! GET IT>>
2. A new evolution in nation-state cybercrime
Nation-state cyberattacks are no longer a problem for just the public sector. An estimated 90% of nation-state cybercrime groups, also known as advanced persistent threat (APT) groups, regularly attack organizations outside of the government or critical infrastructure framework. Russia, North Korea, Iran and China are the four major players in the nation-state cybercrime space, with Russia responsible for 58% of all nation-state attacks in the past year.
In the 2021 Microsoft Digital Defense Report, the company shared valuable insight on the activities of nation-state cybercriminals in 2021 and how their attack patterns are evolving.
- Russian nation-state actors are increasingly effective, jumping from a 21% successful compromise rate in 2020 to a 32% rate in 2021.
- After Russia, the largest volume of attacks observed came from North Korea, Iran and China; South Korea, Turkey (a new entrant) and Vietnam were also active but represent much less volume.
- 21% of attacks observed across nation-state actors targeted consumers.
- 79% of attacks observed across nation-state actors targeted enterprises.
- Rogue states use cyberattacks as a means of generating revenue – North Korea raked in an estimated $1 billion from cybercrime, including more than $400,000 in cryptocurrency.
A recent study by Trellix and the Center for Strategic and International Studies (CSIS) revealed that nearly nine in 10 (86%) organizations believe they have been targeted by a nation-state threat actor. The majority of those hazarding a guess landed on Russia (39%) and China (35%) as the most likely perpetrators of the attacks that they experienced. They also see Russia and China as the most likely points of origin for nation-state attacks that threaten their organization in the next 18 months. The ongoing flood of cyberattacks that have spawned from Russia’s invasion of Ukraine is a good example of how nation-state cybercrime can impact businesses that aren’t in the public sector like broadcast networks, banks, energy companies and other key assets. This will only grow into a bigger concern for businesses in the future.


This MSP-focused guide gives you insight into finding the ideal dark web monitoring solution. GET THE GUIDE>>
3. Phishing just keeps growing more expensive
Businesses are dropping more cash on security these days because of phishing these days even if they don’t fall victim to an attack, and that uptick in expense shows no sign of stopping. The 2021 Ponemon Cost of Phishing Study shed light on the colossal increase in the cost of a phishing attack for businesses. Researchers say that the cost of phishing attacks has almost quadrupled over the past six years, with large U.S. companies losing an average of $14.8 million annually (or $1,500 per employee) to phishing-related expenses. On average, companies lose $1,500 and seven hours of productivity per employee to phishing every year, plus more than 10,000 hours of tech time.
But companies can make a few smart moves that help them save money when it comes to email security. Security awareness training reduces the cost of phishing by more than 50%. It also packs a big punch against security trouble. Companies that engage in regular security awareness training have 70% fewer security incidents. This report also makes it clear that organizations that choose cloud email and cloud-native email security solutions are reaping big cost benefits.
Cost-benefits from the cloud
- Cloud computing is 40x cost-effective compared to in-house IT systems for SMBs.
- Small and medium-sized enterprises enjoy 40% more cost-efficiency from adopting third-party platforms employment rather than maintaining
- Security automation and AI can save businesses more than 80% of the cost of manual security.
Next week in part 2 we’ll look at the risks ahead! Don’t miss it!
Reduce Your Client’s Email Security Risk with Two Heavy Hitters
Anti-Phishing & Security Awareness Training with BullPhish ID
BullPhish ID is the leading phishing simulation solution in the Channel, as well as a smart security and compliance awareness training solution for companies of any size.
- Gain access to a huge library of security and compliance training videos in 8 languages with quizzes to measure retention – and 4 new video lessons are added a month.
- Run phishing simulations easily using plug-and-play or customizable phishing training campaign kits with new kits released regularly.
- Automate the delivery of training to users and the generation and delivery of reports to stakeholders.
- SCHEDULE A DEMO>>
Automated, AI-Enabled Email Security with Graphus
In this dangerous world, every organization needs powerful email security that can stand up to the test of combatting today’s sophisticated threats without a high price tag. Graphus answers that call.
- Put 3 layers of protection between employees and dangerous phishing messages.
- Automated email solutions like Graphus catch 40% more malicious messages than conventional solutions or a SEG.
- AI and machine learning ensure that your clients aren’t waiting on threat reports or patches to be protected from new threats.
- SCHEDULE A DEMO>>
Join the over 4,000 MSPs who are prospering as an ID Agent Partner and you’ll gain access to the best sales enablement program in the business through Kaseya Powered Services.


See how security awareness training grows your MRR + get tips for selling it! WATCH NOW>>


May 26: Building a Foundation of Security: Protect & Train REGISTER NOW>>
Jun 1 Prospecting with Dark Web ID: How to Get Potential Customers to Sit Up and Listen (EMEA) REGISTER NOW>>
Jun 2: Building a Foundation of Security: Document REGISTER NOW>>
Jun 6 – 7: ChannelPro SMB Forum 2022: Southwest (Dallas) REGISTER NOW>>
Jun 6 – 8: IT Nation Secure 2022 REGISTER NOW>>Jun 9: Building a Foundation of Security: Backup & Recover REGISTER NOW>>
Jun 20-23: Connect IT Global in Las Vegas REGISTER NOW>>


It’s a bird, it’s a plane, it’s your revenue rising into the stratosphere with 6 Power-Ups That Will Make You a Sales Superhero. GET IT>>


Email Security is a Key Component of Your Defense
What do ransomware, business email compromise, whaling and account takeover all have in common? They frequently begin with a phishing email. That’s an important reason why email security is an essential component of your organization’s defense.
An estimated 84% of businesses were the victims of a successful phishing attack in 2021. Even worse, about 59% of organizations that fell victim to a phishing attack were then infected with ransomware, and that’s not something that any company can afford to face. But by making smart choices about email security, you can reduce your organization’s risk of trouble.
Strong, effective email security isn’t expensive either. A combination of affordable solutions including automated email security that leverages AI and security automation, plus comprehensive security awareness training that includes phishing simulations helps organizations mount a strong defense that reduces the risk of falling victim to a phishing-based cyberattack.


Do you have comments? Requests? News tips? Complaints (or compliments)? We love to hear from our readers! Send a message to the editor.
ID Agent Partners: Feel free to reuse this post (in part or in its entirety) When you get a chance, email [email protected] to let us know how our content works for you!