What’s the Difference Between Pen Testing and Vulnerability Assessment?

Network penetration testing is crucial for proactively identifying and mitigating security risks. It helps prevent data breaches and financial losses by fortifying an organization’s defenses. Penetration tests allow organizations to assess their cybersecurity posture based on realistic attack scenarios. This enables them to address issues that could lead to a cyberattack or data breach if they followed a solely defensive approach to security.

Learn to defend against today’s sophisticated email-based cyberattacks DOWNLOAD EBOOK>>
What is the difference between penetration testing and vulnerability scanning?
Penetration testing and vulnerability scanning may sound similar, but they’re not the same thing.
Vulnerability scanning is a more passive and automated process that identifies and lists known security vulnerabilities in a system or network. The primary purpose is to discover weaknesses in the target, without actively attempting to exploit them. It provides a snapshot of the system’s security posture at a particular point in time.
Penetration testing (pen testing) is a proactive, simulated attack on a system or network to identify and exploit security vulnerabilities. It attempts to exploit vulnerabilities and provides tangible evidence of potential consequences. The primary goal of penetration testing is to determine the potential impact of a successful cyberattack and to help organizations understand how an attacker might breach their security, giving them insight into vulnerabilities that could lead to a genuine breach – and a chance to fix them before the bad guys use them.
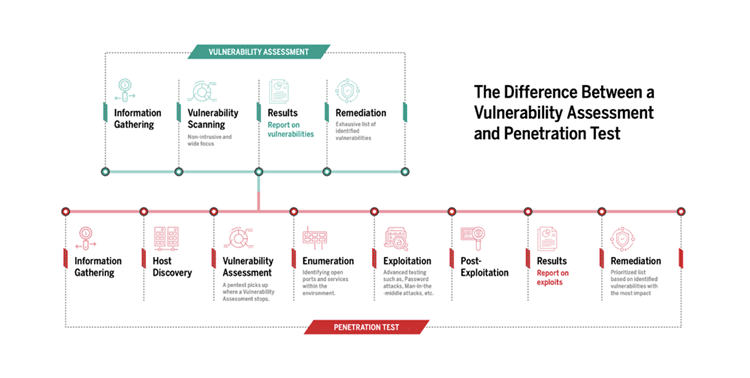
Source: Vonahi

Learn how to identify and mitigate malicious and accidental insider threats before there’s trouble! GET EBOOK>>
Pen testing finds weaknesses that vulnerability scans don’t
By conducting penetration testing, organizations can uncover weaknesses and take steps to address them before they are exploited. A pen test will also reveal what attackers can actually do on the network once access has been obtained, such as viewing sensitive data. This is incredibly valuable information that organizations can only obtain through a penetration test.
Cybercriminals will look for any vulnerability that they can exploit to sneak into a company’s network. This includes some unexpected routes that would not be found by vulnerability scans like:
- Shared local administrator credentials amongst workstations and servers.
- Weak Active Directory domain user account credentials because of a password-based attack.
- Disclosure of employee usernames and/or email addresses on devices like printers.
- Misconfigured all-in-one printers that contain privileged domain account credentials.
- Weak passwords amongst web services, including printers, servers and remote management consoles.
- Misconfigured permissions associated with file shares and services, exposing sensitive data.
Pen testing brings major benefits to the table
According to Tech Republic, one in three companies cited cost as the reason why they don’t conduct more frequent assessments through pen testing. In the past, penetration testing was complex and expensive. Not anymore. Automation and Artificial Intelligence (AI) technology have made penetration testing cheaper. Network penetration testing enhances cyber resilience and offers businesses several benefits including:
- The opportunity to secure the environment and reduce exposure.
- Making it easy to prioritize the remediation of critical security weaknesses.
- Understanding how an attacker could gain access to sensitive data or systems.
- Meeting compliance and regulatory requirements.
- Testing and improving incident response procedures.
- Validating the effectiveness of security controls.
- Avoiding a costly security incident or data breach.
- Peace of mind gained from proactively addressing vulnerabilities.

Is building an in-house SOC a smart move? Our whitepaper breaks down the costs. READ IT>>
Which cyberthreats can be prevented through pen testing?
Here’s a list of some common cyberthreats that can be prevented or mitigated through network penetration testing:
Unauthorized access: Penetration testing can identify weaknesses in authentication mechanisms, such as weak passwords, default credentials or inadequate access controls, which could allow unauthorized individuals to gain access to sensitive systems or data.
Data breaches: Penetration testing helps uncover vulnerabilities in data storage, transmission and processing systems, reducing the risk of data breaches due to insecure configurations, unencrypted data or inadequate data protection measures.
Malware infections: Penetration testing can identify vulnerabilities that could be exploited by malware, such as unpatched software, misconfigured security settings or weak perimeter defenses, helping to prevent malware infections, ransomware attacks and subsequent damage.
Denial of Service (DoS) attacks: Penetration testing can assess the resilience of network infrastructure against DoS attacks by identifying and mitigating vulnerabilities that could be exploited to disrupt services or overload network resources.

Learn how to spot today’s most dangerous cyberattack & get defensive tips in Phishing 101 GET EBOOK>>
Man-in-the-Middle (MitM) attacks: Penetration testing can identify weaknesses in network encryption protocols, certificate management or insecure network configurations that could be exploited by attackers to intercept and manipulate communications between parties.
Insider threats: Penetration testing can assess the effectiveness of access controls and monitoring mechanisms in detecting and preventing insider threats, such as unauthorized access by employees or contractors with malicious intent.
SQL injection: Penetration testing can identify vulnerabilities in web applications and database systems that could be exploited by attackers to execute arbitrary SQL queries, potentially leading to unauthorized access to sensitive data or manipulation of database contents.
Cross-Site Scripting (XSS): Penetration testing can identify vulnerabilities in web applications that could be exploited to inject malicious scripts into web pages viewed by other users, potentially leading to the theft of sensitive information or unauthorized actions on behalf of users.
Phishing attacks: Penetration testing can assess the effectiveness of security awareness training and phishing detection mechanisms in detecting and mitigating phishing attacks, which attempt to trick users into divulging sensitive information or downloading malware.
IoT vulnerabilities: Penetration testing can identify vulnerabilities in Internet of Things (IoT) devices and networks, reducing the risk of exploitation by attackers to gain unauthorized access to IoT devices, compromise data privacy, or launch attacks against other systems.

Learn more about growing supply chain risk for businesses and how to mitigate it in a fresh eBook. DOWNLOAD IT>>
Kaseya’s Security Suite Helps Businesses Mitigate All Types of Cyber Risk Affordably
Kaseya’s Security Suite has the tools that MSPs and IT professionals need to mitigate cyber risk effectively and affordably, featuring automated and AI-driven features that make IT professionals’ lives easier.
BullPhish ID — This effective, automated security awareness training and phishing simulation solution provides critical training that improves compliance, prevents employee mistakes and reduces a company’s risk of being hit by a cyberattack.
Dark Web ID — Our award-winning dark web monitoring solution is the channel leader for a good reason: it provides the greatest amount of protection around with 24/7/365 human and machine-powered monitoring of business and personal credentials, including domains, IP addresses and email addresses.
Graphus — Automated email security is a cutting-edge solution that puts three layers of AI-powered protection between employees and phishing messages. It works equally well as a standalone email security solution or supercharges your Microsoft 365 and Google Workspace email security.
RocketCyber Managed SOC — Our managed cybersecurity detection and response solution is backed by a world-class security operations center that detects malicious and suspicious activity across three critical attack vectors: endpoint, network and cloud.
Datto EDR — Detect and respond to advanced threats with built-in continuous endpoint monitoring and behavioral analysis to deliver comprehensive endpoint defense (something that many cyber insurance companies require).
Vonahi Penetration Testing – How sturdy are your cyber defenses? Do you have dangerous vulnerabilities? Find out with vPenTest, a SaaS platform that makes getting the best network penetration test easy and affordable for internal IT teams.
Learn more about our security products, or better yet, take the next step and book a demo today!

Read case studies of MSPs and businesses that have conquered challenges using Kaseya’s Security Suite. SEE CASE STUDIES>>

Our Partners typically realize ROI in 30 days or less. Contact us today to learn why 3,850 MSPs in 30+ countries choose to Partner with ID Agent!
Check out an on-demand video demo of BullPhish ID or Dark Web ID WATCH NOW>>
See Graphus in action in an on-demand video demo WATCH NOW>>
Book your demo of Dark Web ID, BullPhish ID, RocketCyber or Graphus now!